Blog
 Et Tu, Root? Exim Announces Yet Another CVE
Et Tu, Root? Exim Announces Yet Another CVE9. September 2019
Users are hit with an announcement of yet another Exim vulnerability. This is the second major occurrence that put the spotlight on Exim in less than three months.
 The Return of the WIZard: Critical Remote Command Execution Vulnerability Impacts Old Exim Installations
The Return of the WIZard: Critical Remote Command Execution Vulnerability Impacts Old Exim Installations7. Juni 2019
Security researchers from Qualys discovered and reported a critical remote command execution (RCE) security flaw that directly affects Exim, a mail transfer agent (MTA) that relays emails from senders to recipients.
 An April Fool’s Joke That Highlights Why We Are So Vulnerable Online, Even If We Check The News
An April Fool’s Joke That Highlights Why We Are So Vulnerable Online, Even If We Check The News1. April 2019
On this special day, April the 1st, I want to talk about the latest “news”. In the past couple of days, media got flooded with articles like “Email addresses of almost a BILLION people are leaked in one of the biggest data breaches ever”. Although data…
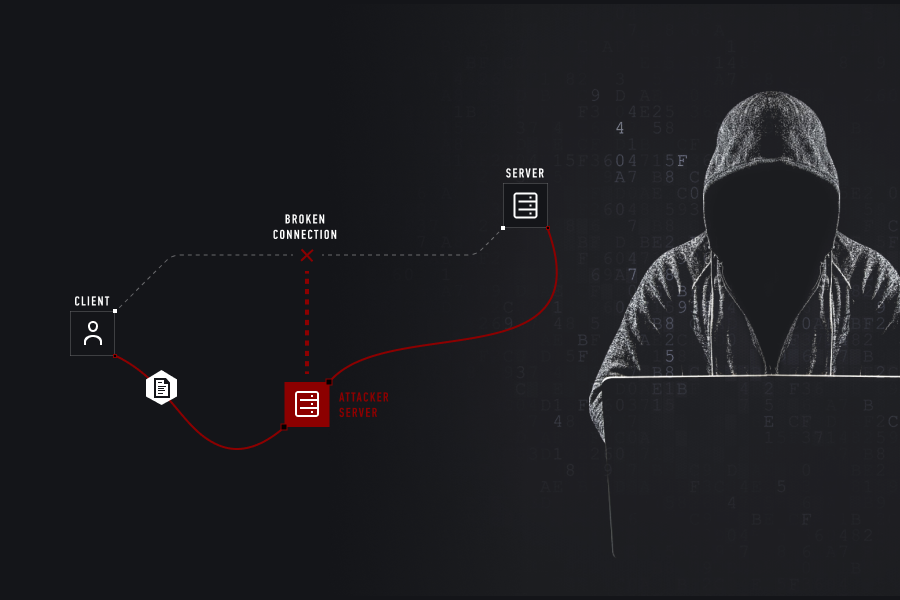 How To Protect Emails From Man-In-The-Middle (MITM) Attack
How To Protect Emails From Man-In-The-Middle (MITM) Attack20. Februar 2019
There are plenty of problems we face in our daily lives, but some of them are more obvious than others. One problem you might not even be aware of is your email – and the threat it poses to your organization's cybersecurity. In particular, the threat of…
 Three Marching Steps Towards Complete SOX Compliance
Three Marching Steps Towards Complete SOX Compliance6. Februar 2019
Compliance is without a shadow of a doubt a cornerstone of every modern business model. So many enterprises are falling short in their aspirations to “touch the sky” after failing to play by the government-established rules.
 GDPR Email Compliance: A Necessity of Modern Business Life
GDPR Email Compliance: A Necessity of Modern Business Life4. Februar 2019
Games that have too many rules usually don’t stick with people, but the business game is an exception. One could say that it has a pile of regulations and absolutely no mercy – and would be right.
 Phishing Attacks Prevention: How To Protect Your Enterprise Against Phishing Attacks
Phishing Attacks Prevention: How To Protect Your Enterprise Against Phishing Attacks30. Januar 2019
As email continues to be the most common vector of all social cyber-attacks (96%), phishing has become increasingly common. According to a recent Verizon report, phishing and pretexting actually represent 98% of social incidents and 93% of breaches.
 How Not to Get on the Phishing Hook of the Internet Fraudsters
How Not to Get on the Phishing Hook of the Internet Fraudsters24. Januar 2019
How often do you follow the wise advice from the “Measure Twice, Cut Once” proverb? And this one: “Trust, but Verify”? After the incident that happened to me, I could say I did become wiser.
 How to Recall an Email in Outlook With StealthMail
How to Recall an Email in Outlook With StealthMail22. Januar 2019
I recently wrote a message, attached an annual financial report to it and clicked Send. One second later, a genius idea crossed my mind – to check the report for orthographic mistakes. All I could think afterward was: “What was I thinking when I clicked…
⨯
