Blog
 Everything You Need To Know About How To Send Encrypted Email
Everything You Need To Know About How To Send Encrypted EmailDecember 18, 2019
‘How do I send an encrypted email?’ – the question that keeps popping up online every now and then and is yet to receive a definitive answer.
 How To Stop Being Afraid of Data Encryption and Start Using It As Your Advantage
How To Stop Being Afraid of Data Encryption and Start Using It As Your AdvantageDecember 11, 2019
Debunk the most formulaic fears connected with data encryption and find out how it could become your reliable business partner.
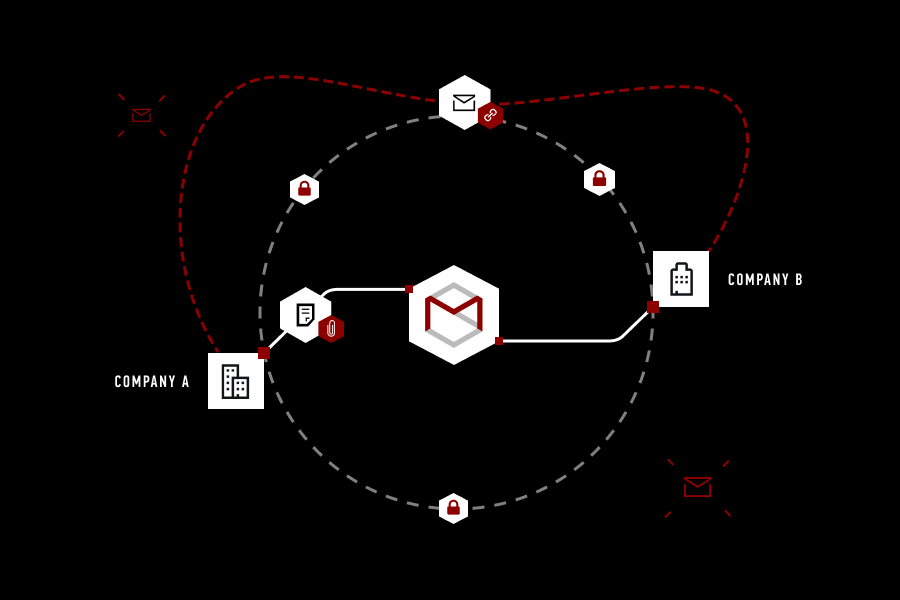 Explaining StealthMail’s Approach To Email Security
Explaining StealthMail’s Approach To Email SecurityDecember 4, 2019
There are a lot of email security services on the market, and most of them deserve some spotlight.
 StealthMail: Email Is No Longer The Weakest Cybersecurity Link
StealthMail: Email Is No Longer The Weakest Cybersecurity LinkNovember 27, 2019
We use trusted express mail and courier services whenever there is an urgent need to privately deliver documents.
 How StealthMail Protects You From Email Threats
How StealthMail Protects You From Email ThreatsNovember 20, 2019
In the past few years, a filtering system from spam messages was substantially upgraded, plus user experience on mobile email clients also saw some improvements. But even with all that, 91% of worldwide cyber-attacks are coming to life through phishing…
 StealthMail Is Invited To Participate In The Regional Cyber Resilience Forum During Moldova’s Cyber Week 2019
StealthMail Is Invited To Participate In The Regional Cyber Resilience Forum During Moldova’s Cyber Week 2019November 20, 2019
On November 19-20 the Regional Cyber Security Forum is going to take place within the 7th edition of “Moldova Cyber Week 2019” in Chisinau, Moldova.
 UA.SC 2019: Evgen Verzun Defines Cybersecurity Criteria for Secure Solutions for 2020 and Beyond
UA.SC 2019: Evgen Verzun Defines Cybersecurity Criteria for Secure Solutions for 2020 and BeyondNovember 15, 2019
November 14, 2019, Evgen Verzun, CTO of StealthMail, attended UA SC 2019 in Kyiv, Ukraine. UA SC Conference is an annual cybersecurity event where key security experts and business owners share their experience building comprehensive corporate…
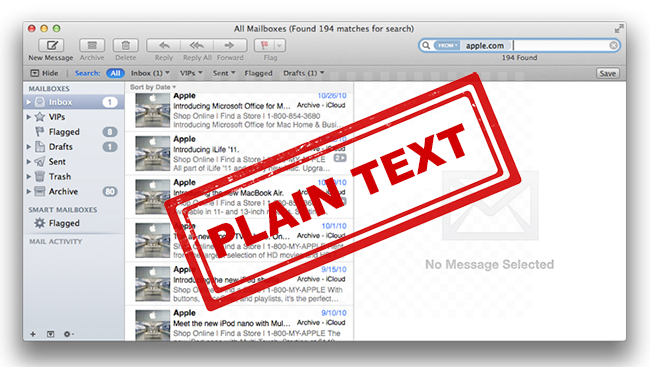 Apple Mail Secrets Explained In Plain Text
Apple Mail Secrets Explained In Plain TextNovember 8, 2019
Apple Mail stores encrypted emails in plain text database, no private key required to read emails
 Exim, Do You Ever Have Deja Vu? I Do!
Exim, Do You Ever Have Deja Vu? I Do!October 3, 2019
Groundhog Day is still months away, but it feels like we are in a time warp just like Phil Connors. That’s because Exim has reported yet another critical vulnerability, the second one this month alone.
⨯
