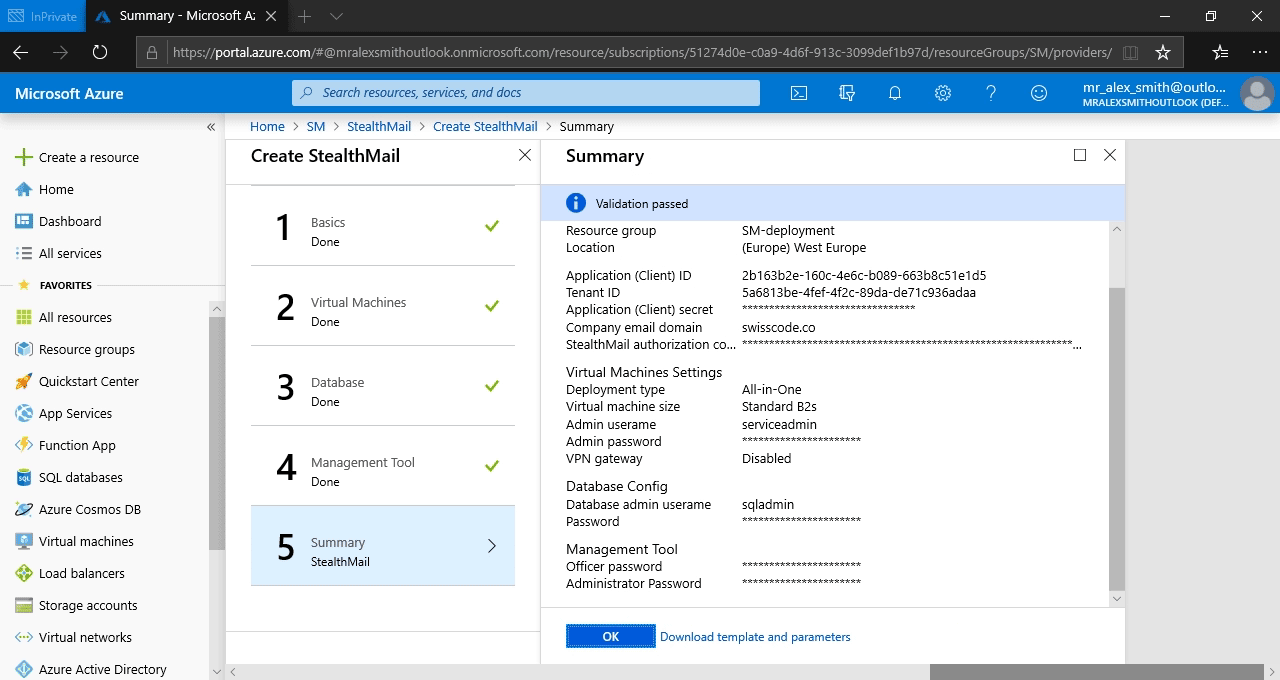
Deployment to Azure
Once you found StealthMailAMA in the Microsoft Azure Marketplace, you should select a Plan in the first place. It would be a wise to chose plan that fits close enough the number of your internal and external users.
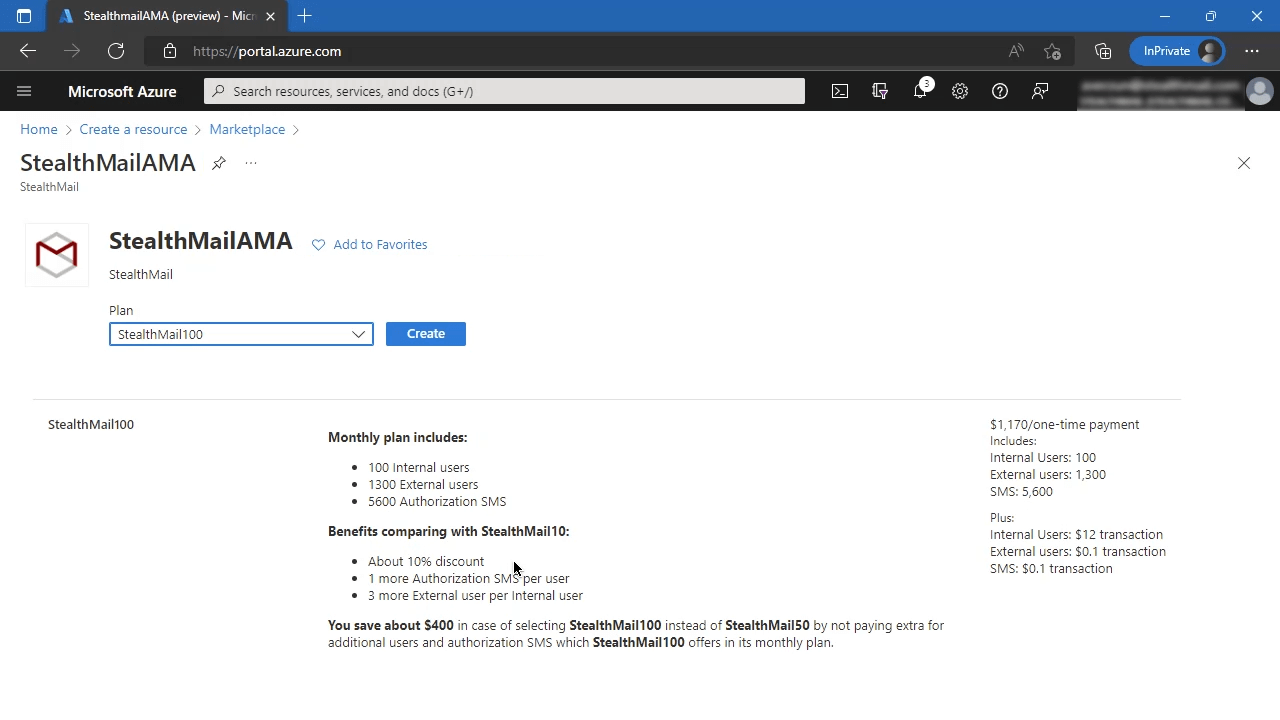
To deploy StealthMail in your Azure cloud you will need to run the wizard and fill out the required fields.
Initial
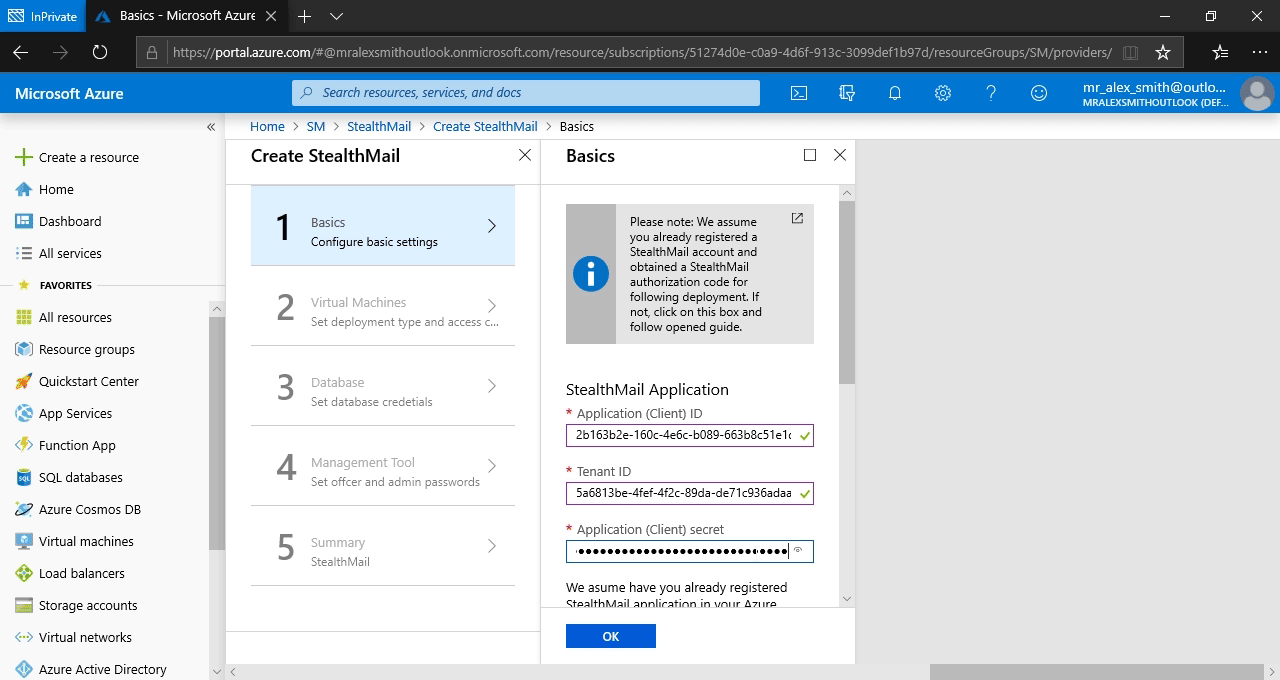
Add Application (Client) ID, Tenant (Directory) ID and Application Secret in the input fields. These are values you got and saved after registering the StealthMail application in the Azure Active Directory.
Company email domain - it is a main company domain that you set after domain validation on StealthMail website.
StealthMail authorization code - a code you received while completing the last step in the deployment guide on StealthMail website.
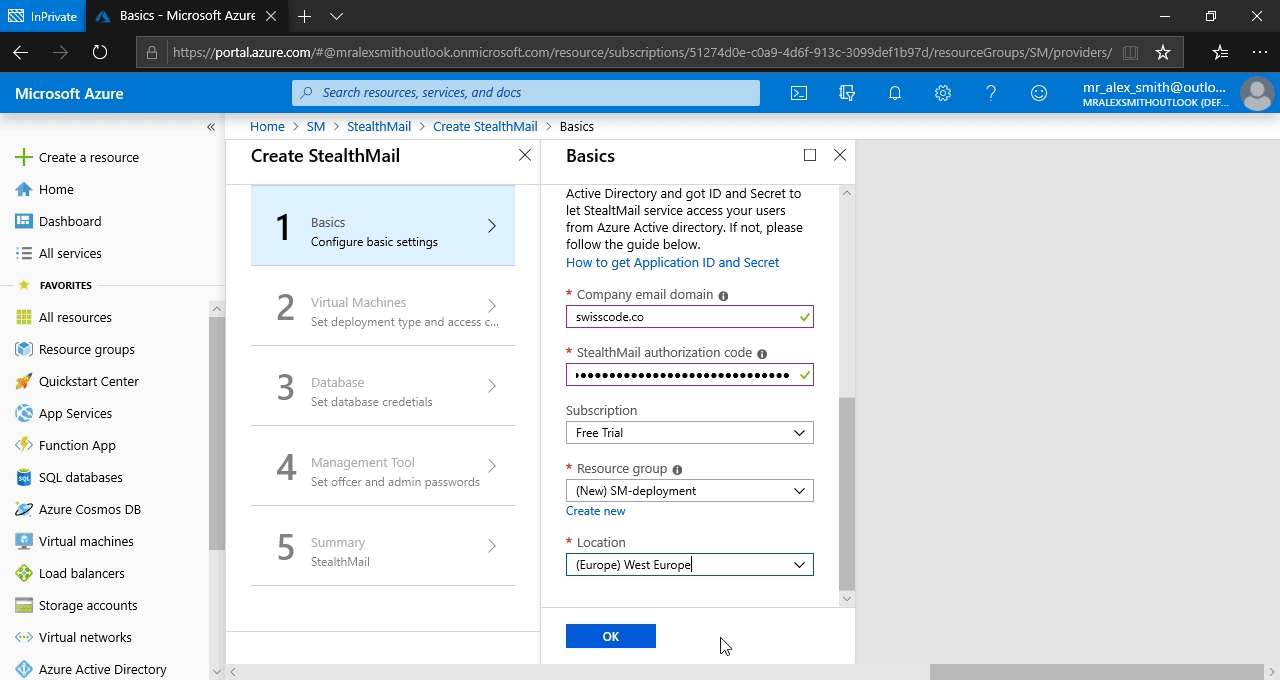
Subscription - If you have several active subscriptions, choose the one where you plan to deploy StealthMail.
Resource group - click Create new - to create a new resource group specifically for StealthMail, it is critical.
Location - pick the region that is the closest to your actual location, this will ensure the best possible connection speed.
Virtual Machines
Deployment Type - Choose a Distributed option to get a better performance. It will use three VMs for StealthMail deployment.
StealthMail Virtual Machines - Pick the size of the cloud VM. B2s would be enough for about 50 users, choose more powerful machines for more users.
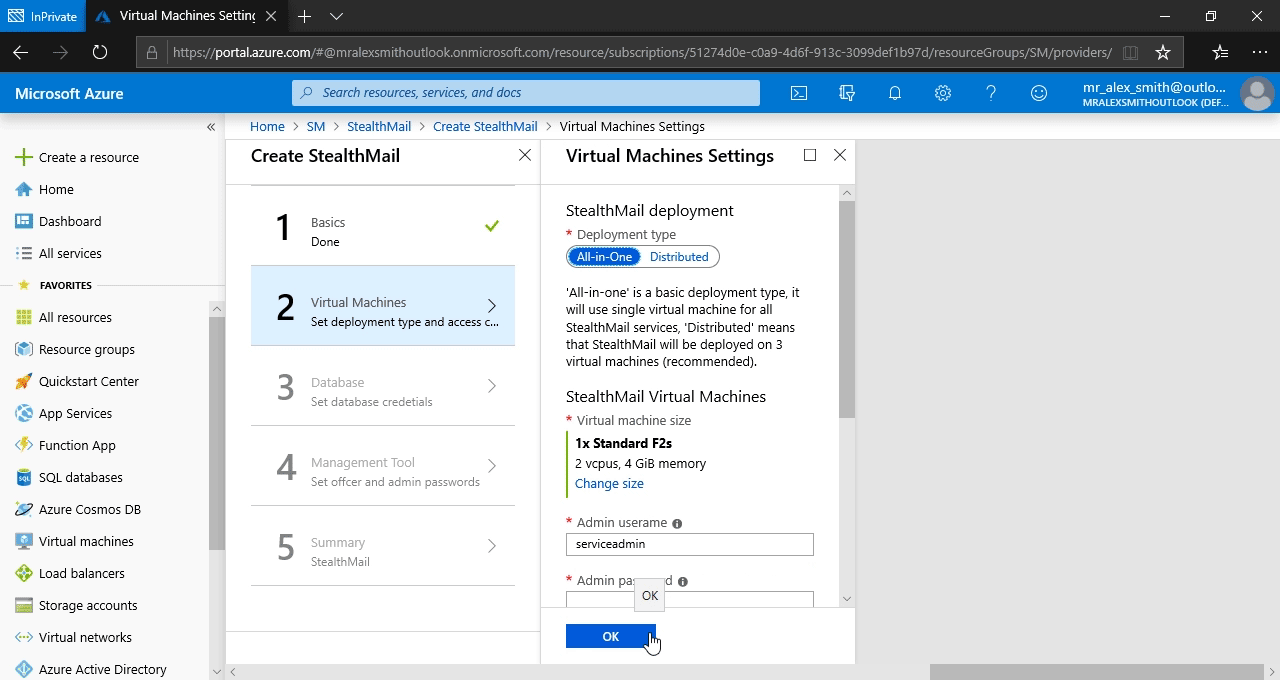
Admin username and Admin password - Specify StealthMail Virtual Machines administrator name and password. These credentials will be used to log in to virtual machines to manage them, if required.
Secure Gateway to StealthMail VMs - If enabledm it allows you to configure a secure VPN to StealthMail infrastructure.
Read more about VPN gateway and its configuration here https://docs.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-about-vpngateways
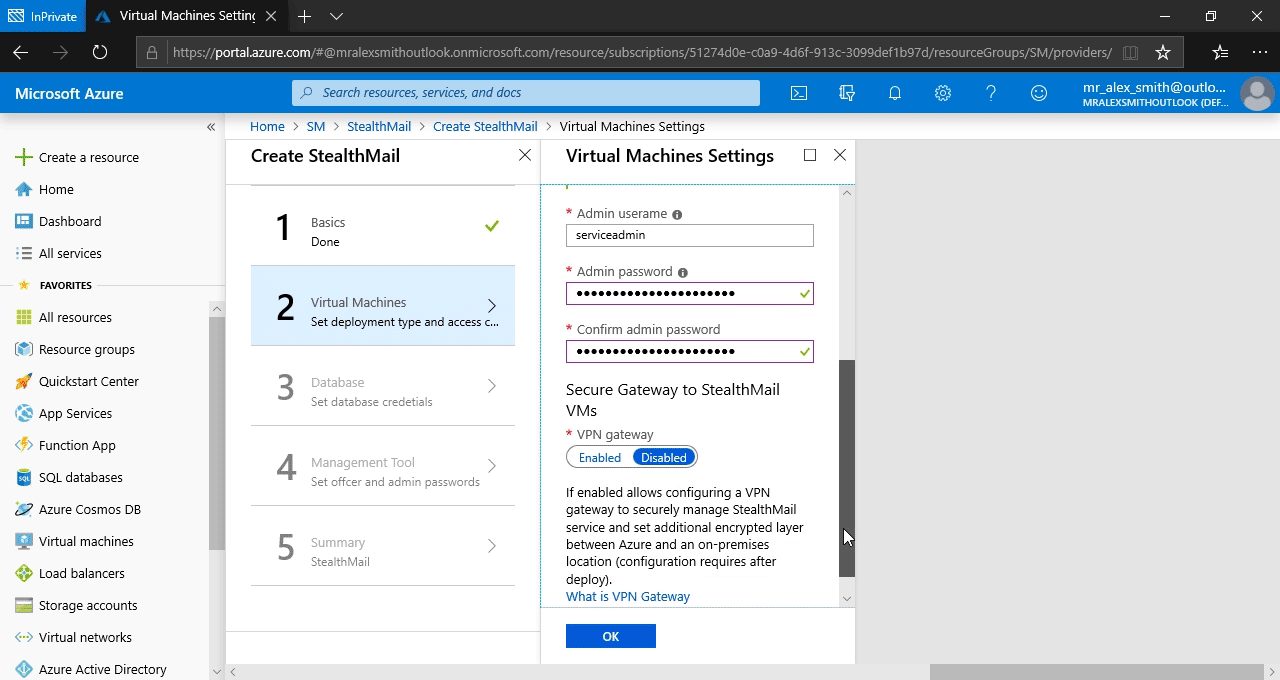
Database Configuration
Database admin username and Password - Credentials to access StealthMail database
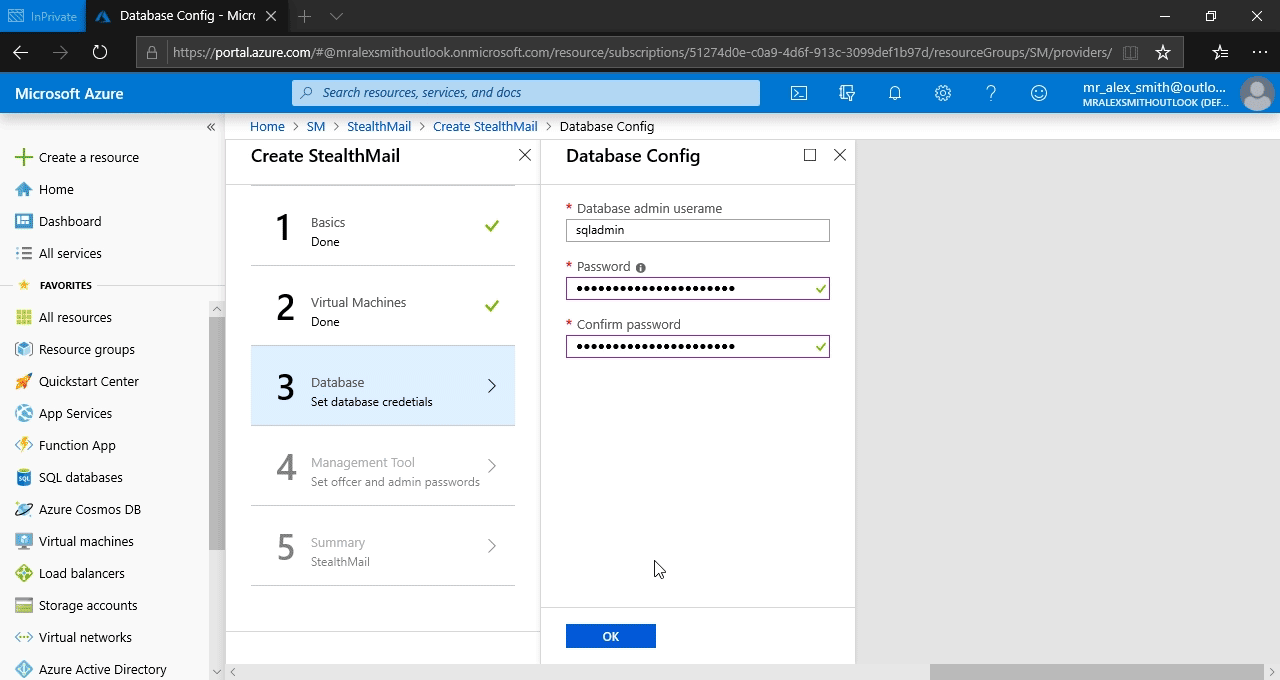
Management tool
StealthMail Management Tool is an application developed for Security officers and company administrators. It allows to manage StealthMail users e.g. change their passwords, set limits on the number of devices and get the information about them.
Set credentials for your company’s security officer and administrator for StealthMail Management tool.
That’s it. You may proceed to StealthMail deployment and Click OK.
If client applications have connection issues with the StealthMail service after the deployment, please refer to this troubleshooting page.