Advanced Email Security for Office 365
StealthMail provides enterprise email security to help businesses prevent breaches of data, protect against advanced attacks, and mitigate human error.
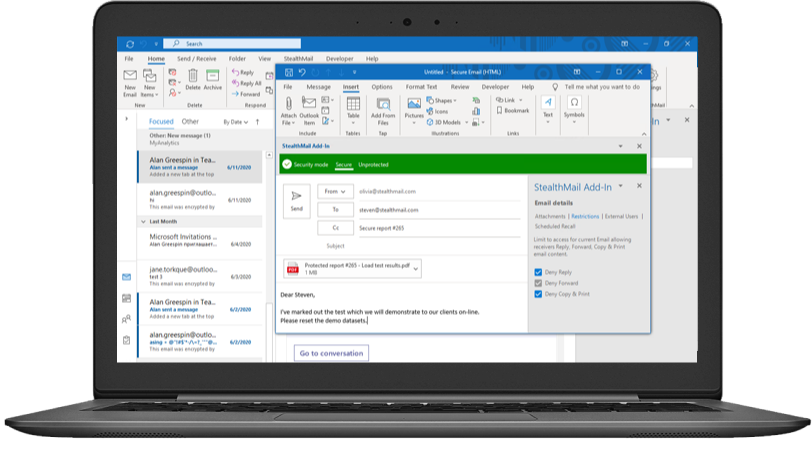
End-to-End Encryption for Outlook
Messages sent with StealthMail are encrypted on device, in transit and stored in encrypted form in the protected cloud.


Encryption Key Ownership
Encryption keys are owned exclusively by the client company. Neither Microsoft, nor StealthMail can access secure content.
Shared Data Control
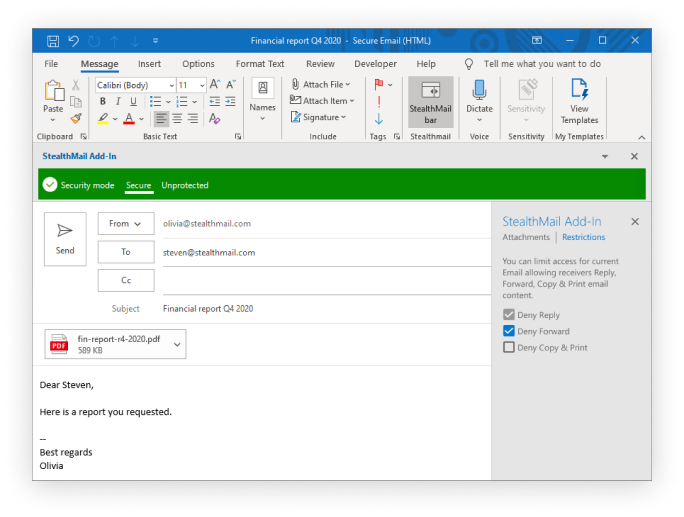
Restrict the recipient’s ability to reply, forward, copy & print secure emails or completely revoke all access to email content and its attachments.
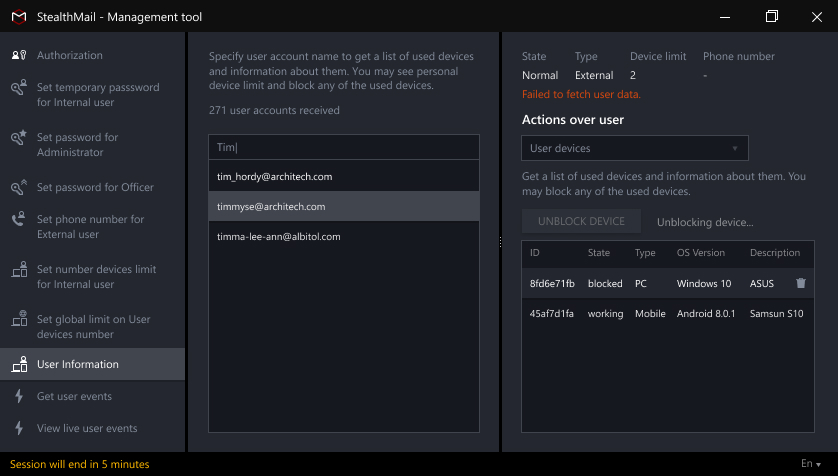
Powerful User Management
The Officer Tool allows to monitor user activity, events and devices, manage access and mitigate human error.

Deployed Under 2 Hours*
StealthMail is quickly and easily deployed in Azure Cloud without affecting existing email infrastructure.
*On average. Depending on your domain registrar, it may take up to 72 hours for your domain to be verified.
Shortcomings of Traditional Email Communication
Advantages of StealthMail Email Security
⨯
Start free trial
