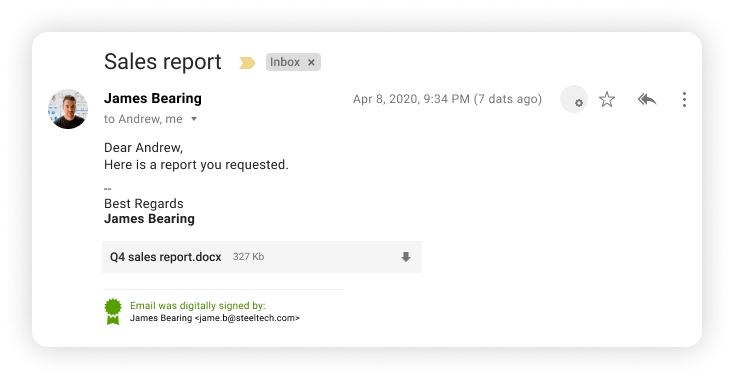
Meet Data Protection, Email Security, and Privacy Compliance in Gmail
StealthMail helps enterprises secure communication with patented data transfer technology SDNP to mitigate email security risks associated with cyber-attacks as spear phishing, email spoofing, and man-in-the-middle.
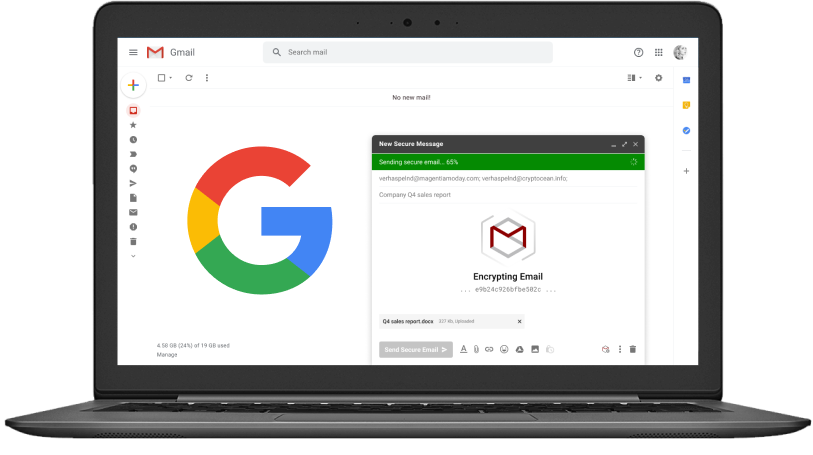
End-to-End Encryption for Gmail
Messages sent with StealthMail are end-to-end encrypted on device, at rest, and in transit. Neither Google, nor StealthMail can access secure content.
End-to-End Encryption for Gmail
Messages sent with StealthMail are end-to-end encrypted on device, at rest, and in transit. Neither Google, nor StealthMail can access secure content.

Instant Availability
The StealthMail App for Microsoft makes all features of StealthMail conveniently accessible right within Microsoft Teams.
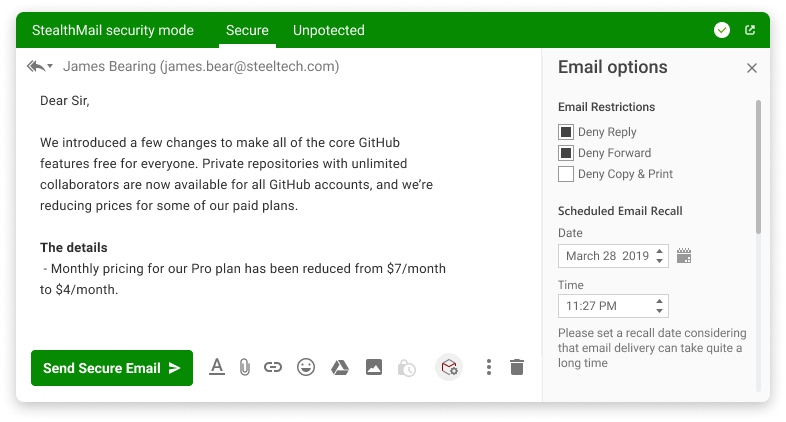
Powerful Data Control
Email content is stored in a protected cloud and only secure Stealth-links are sent to recipients. Such links can be disabled and access to email content revoked at any time.
Powerful Data Control
Email content is stored in a protected cloud and only secure Stealth-links are sent to recipients. Such links can be disabled and access to email content revoked at any time.
Regulatory Compliance
Send CCPA-, HIPAA-, GDPR-compliant emails and securely share sensitive information with contacts inside and outside of your organization.
EU GDPR
General Data Protection Regulation
SOX
Sarbanes Oxley Act
HIPAA
Health Insurance Portability and Accountability Act
GLBA
Gramm-Leach-Bliley Act
Reg FD
Regulation Fair Disclosure
Shortcomings of Traditional Email Communication
Advantages of StealthMail Email Security
⨯
Start free trial