Get officer tool
StealthMail Officer Tool is an application that allows to manage StealthMail users e.g. change their passwords, set phone number for external users, set limits on the number of devices and preview the latest user events.
To let your company’s administrators and security officers use it, first you should export secret keys binaries. They will be used by administrators and security officers during the login process. Along with access keys, service keys will be exported. These keys are used to additionally protect the company data.
Please note: Please save all of them in your protected storage. If something happens with Azure vault, you may re-upload them from your backup.
Get the rights to export keys
In Azure portal go to the resource group that you created during StealthMail deployment.
Click on Resource groups list item, then, in the new pane, on the StealthMail’s resource group.
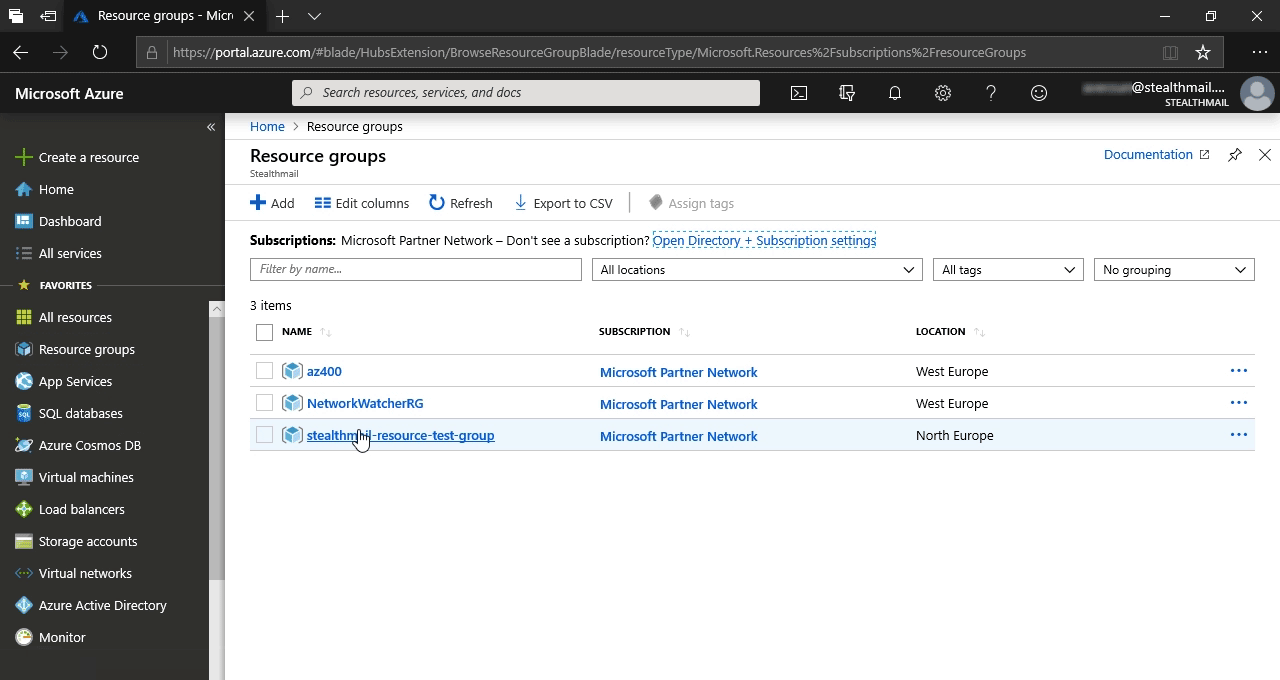
Scroll down the list to the Key vault item and click on it. It should be named like StealthMail####### where # - is a random character or a digit.
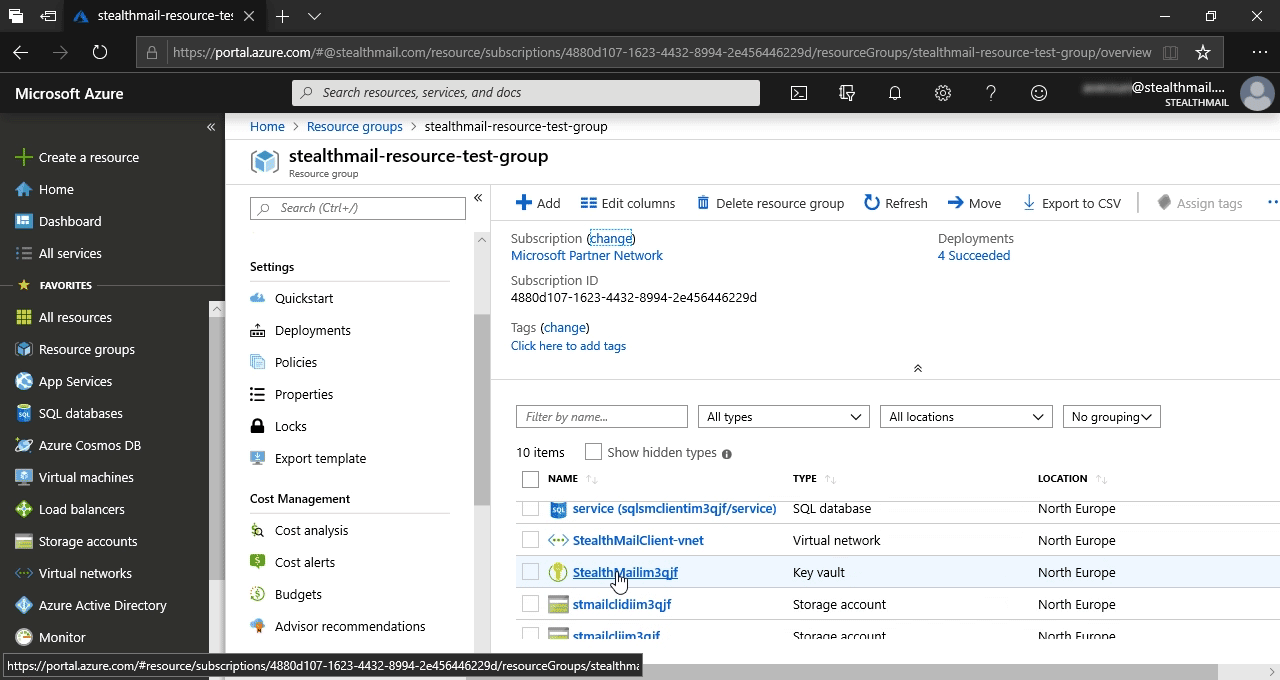
In the list, find and click on the Access policies item.
Then, in the new pane, click on the + Add Access Policy button.
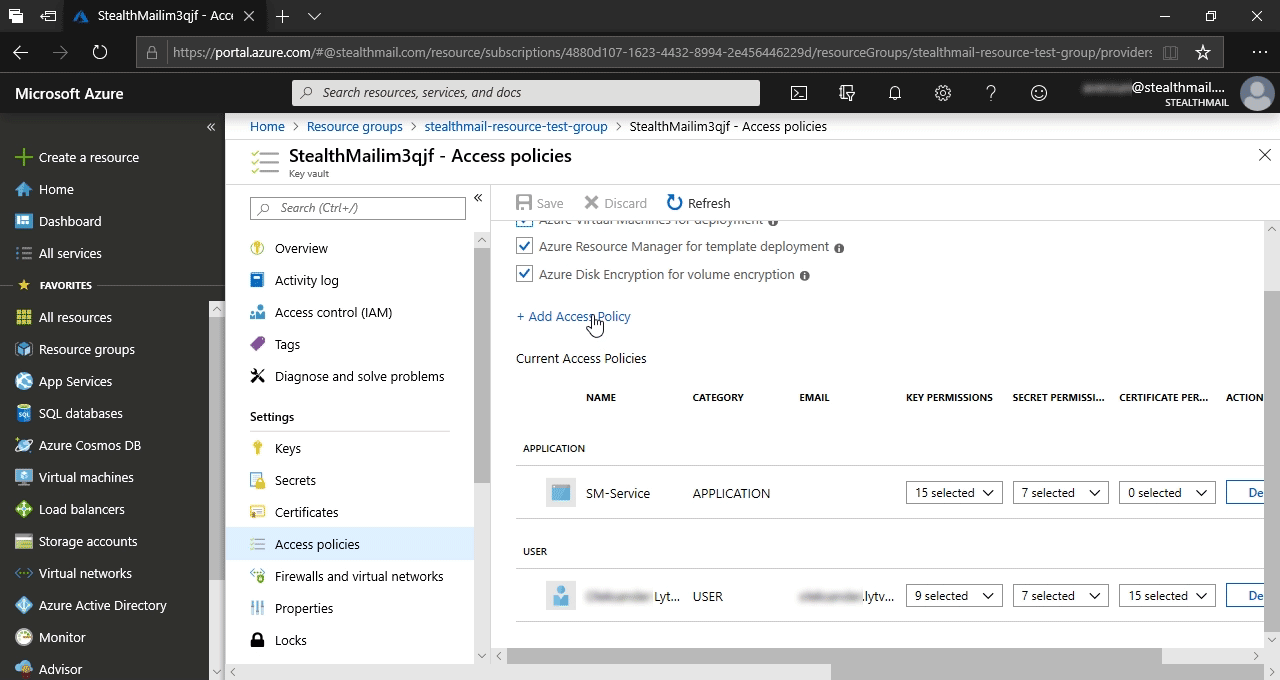
In the new pane, fill the form this way:
- In the field Configure from template - choose Secret Management;
- In the field Secret permission - choose Get;
- Click Select principal and select in the right pane a user account that will be used to export secret keys, then click on the Select button.
- Leave the default values in the remaning fields of the pane.
- At the very bottom of the main form click on the Add button.
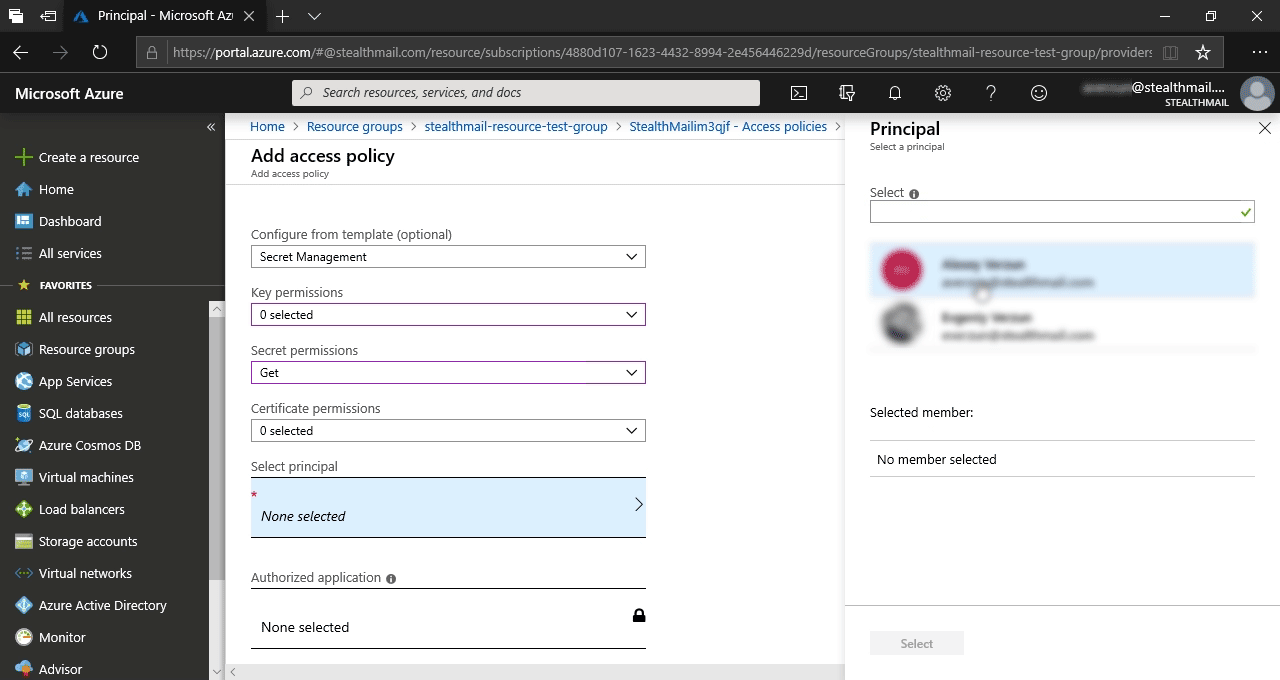
You will be redirected to the previous pane (Access Policies).
Click on the Save button.
Now you are ready to extract the secret keys.
Extracting keys
Get a powershell script to extract the keys using one of the links below.
Get_SM_Keys_From_KeyVault.ps1- for the latest Windows 10, Windows Server 2016/2019 versions.
Get_SM_Keys_From_KeyVault_AzureRMbased.ps1- for early Windows operating systems.
Run PowerShell with Administrator permissions.
Then run a script with the following command:
powershell -ExecutionPolicy ByPass -File Get_SM_Keys_From_KeyVault.ps1, where -File parameter should contain a path to the powershell.
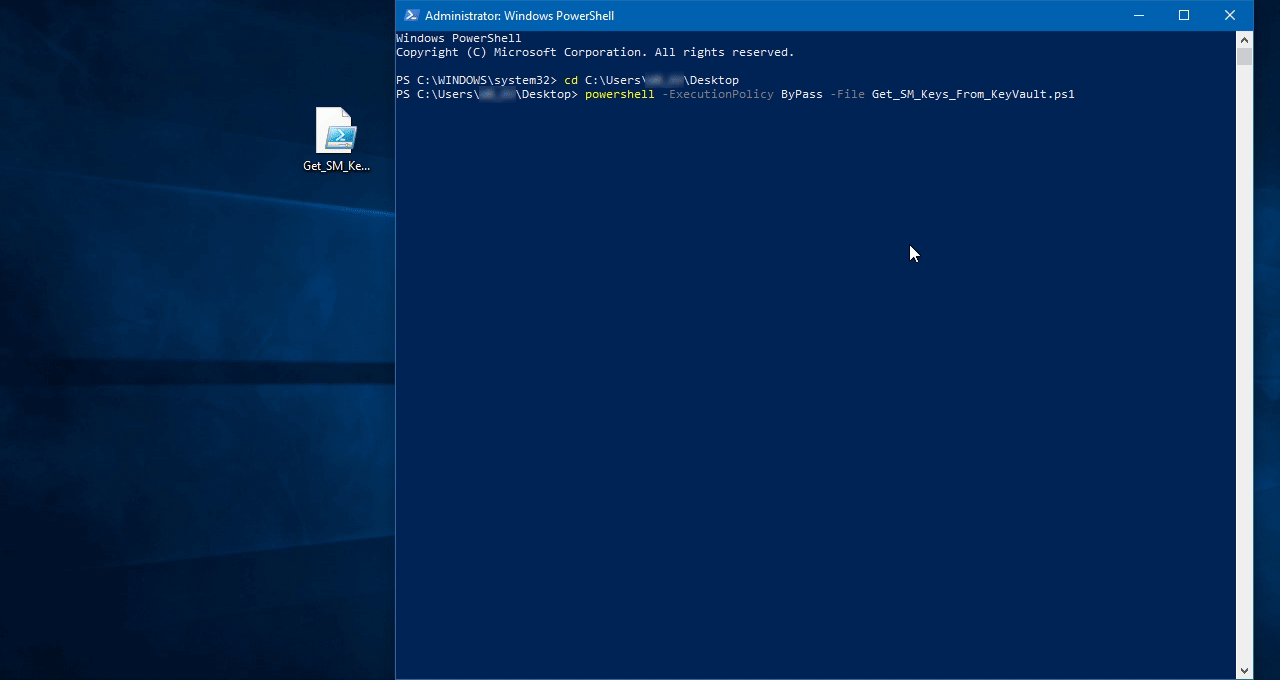
When prompted, enter the destination path and KeyVault name StealthMail####### from the StealthMail resource group.
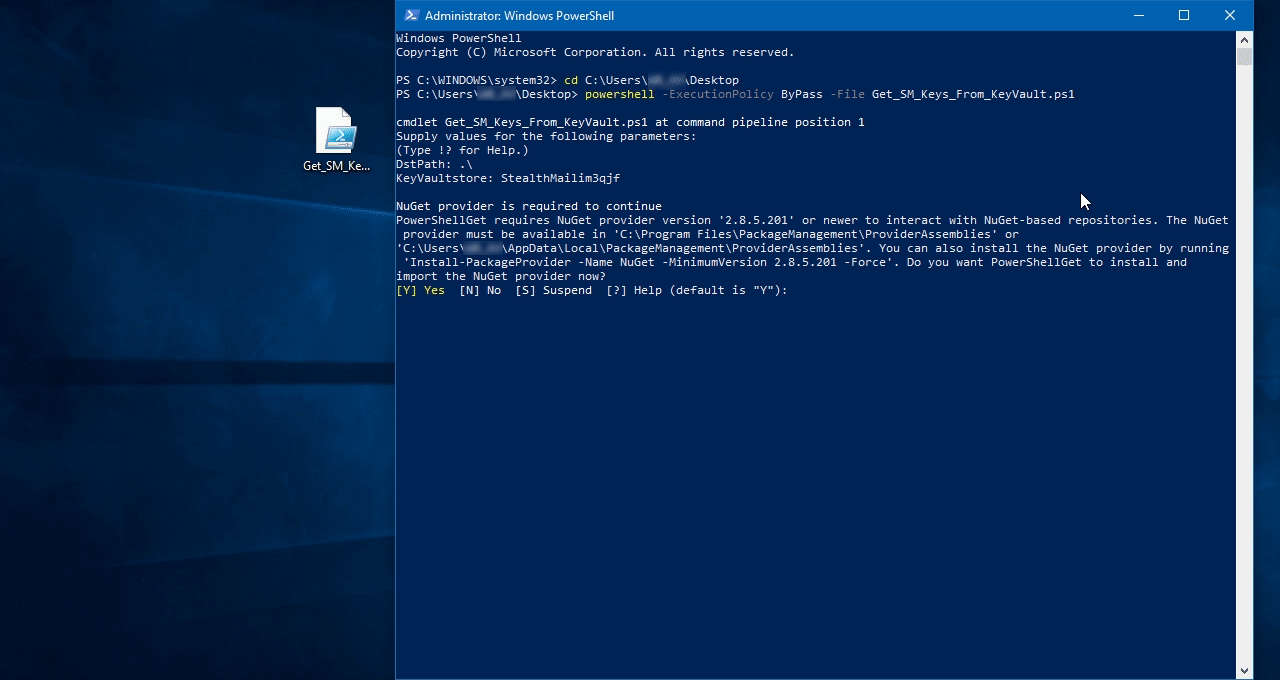
It is possible that your system may not have the required modules and you will be asked to download them from Microsoft repositories.
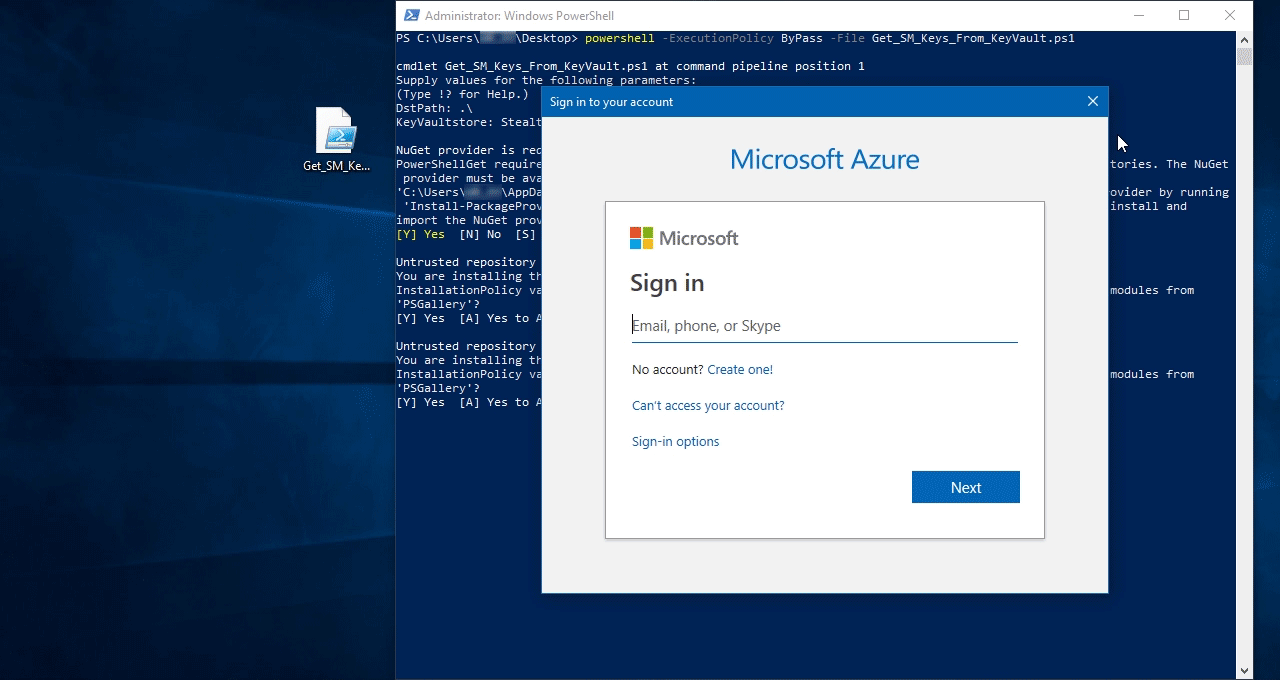
Use your account credentials that you provided as principal when granting access rights in the previous step. They are required to access StealthMail KeyVault and extract the secret keys.
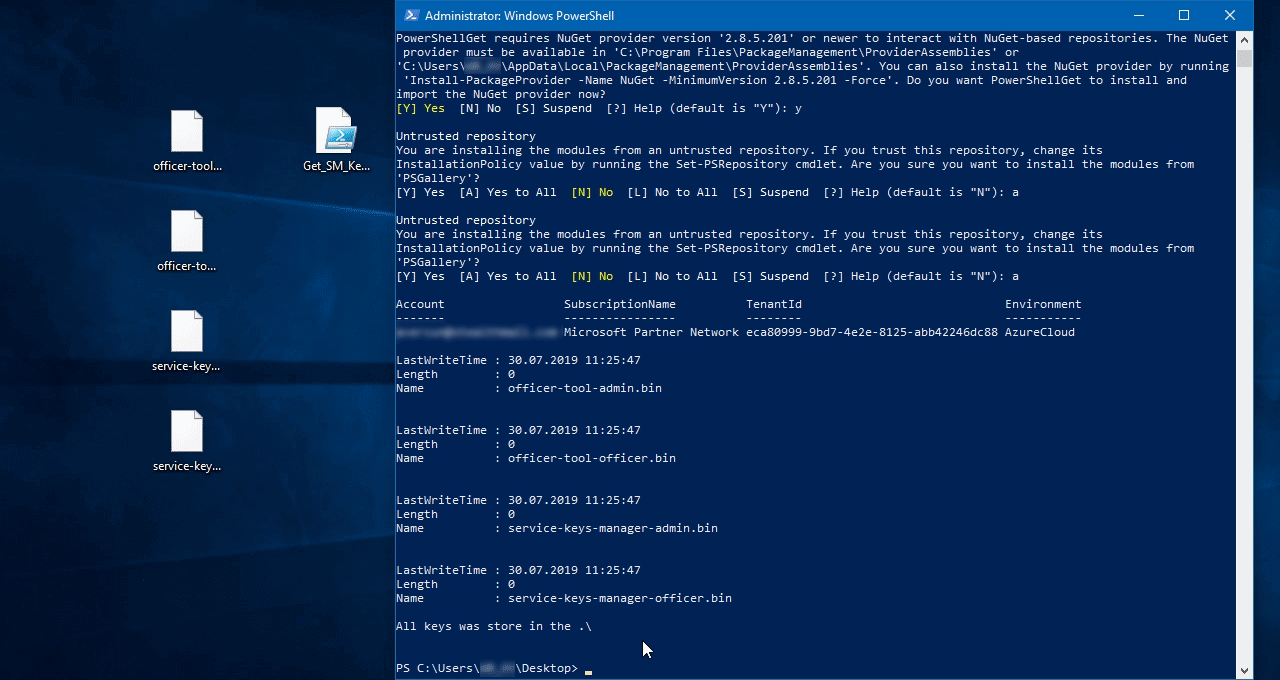
As a result, you give the admininstrator and the security officer secret access keys for the Officer tool:
- officer-tool-officer.bin
- officer-tool-admin.bin
These keys will be used in the Officer tool to login and manage StealthMail users.
And service keys pair:
- service-keys-manager-officer.bin
- service-keys-manager-admin.bin
These keys are used to additionally protect stored encrypted users and company data.
Please note: Please save all of them in your protected storage. If something happens with Azure vault you may re-upload them from your backup.
Now you are ready to download the Officer tool and to configure it for the first run.
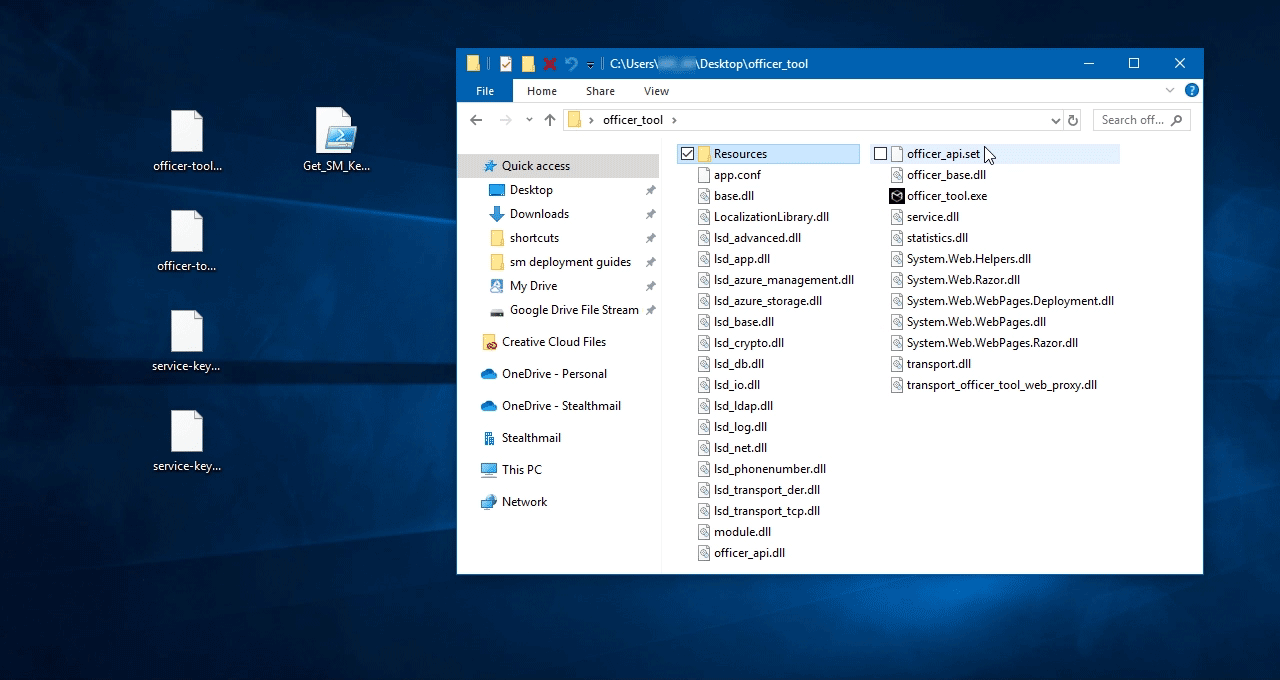
You need to set officer_api_webProxyIp with an IP address of the VM where StealthMail is deployed.
To get the VM IP address, go back to StealthMail resource group and scroll to SM-Service VM list item, then click on it.
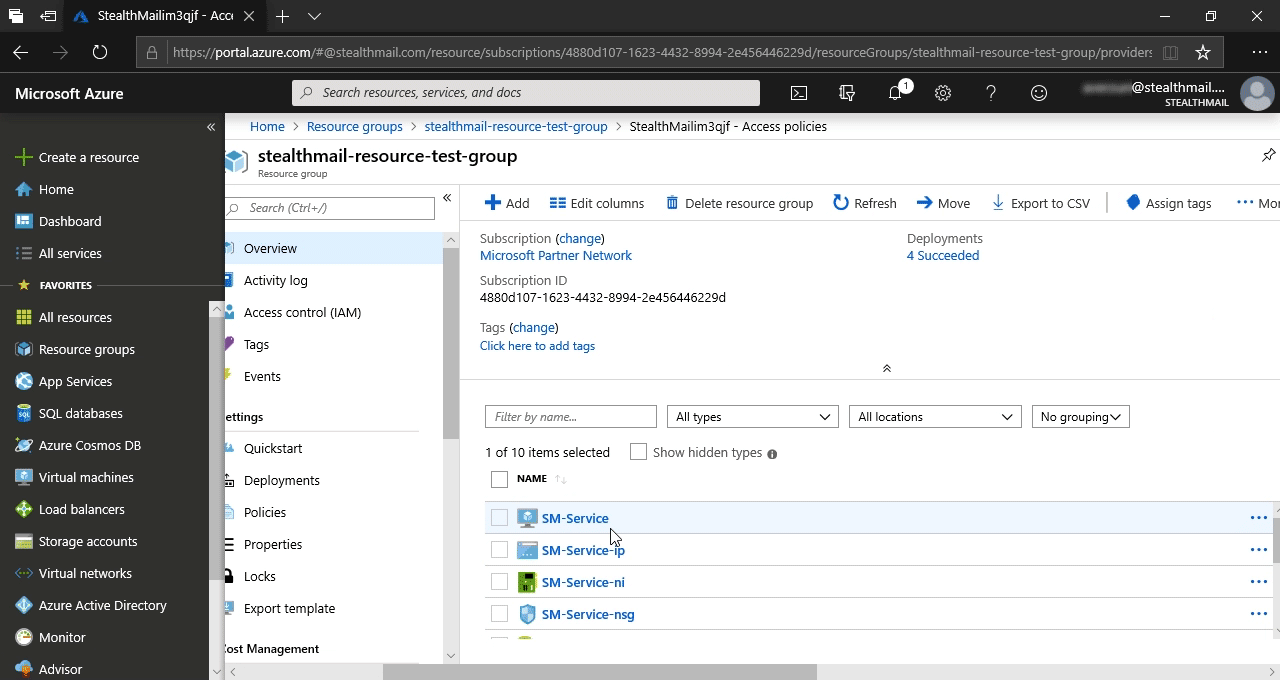
Copy Public IP address from the Overview information and paste it to the recently opened officer_api.set.
Save changes and close the file.
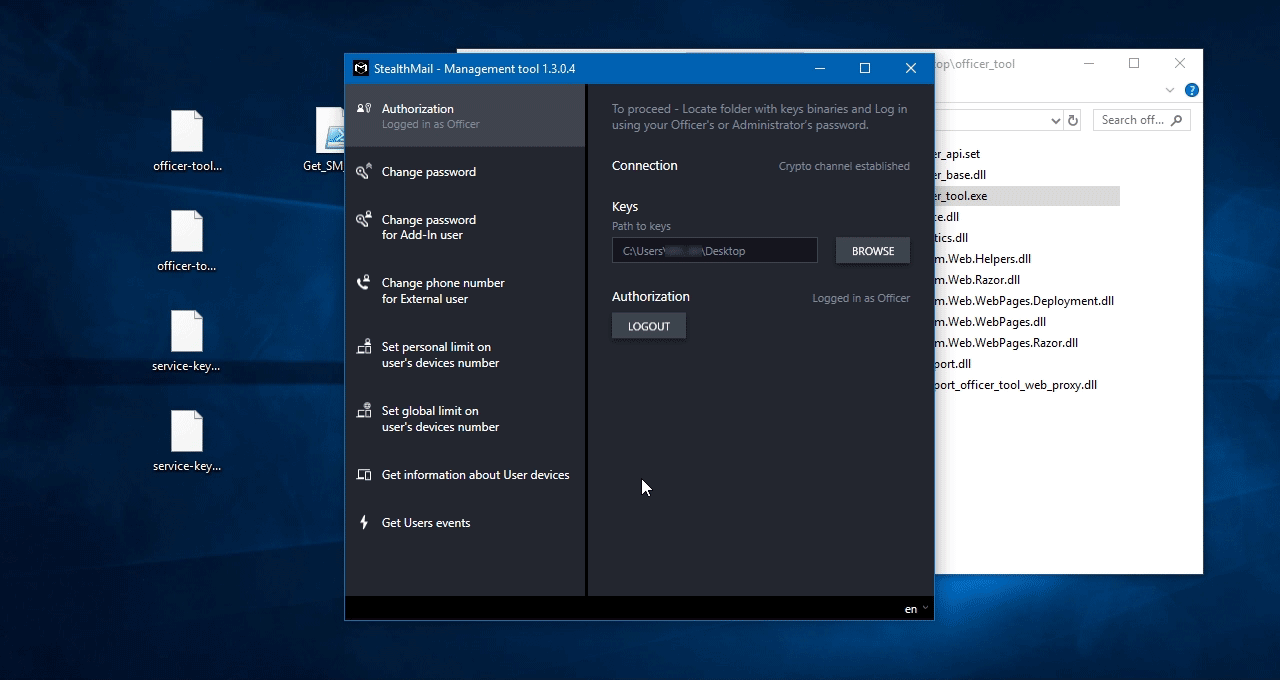
Run officer_tool.exe
To log in - choose a folder where you have saved the extracted access keys.
Enter Administrator or Security officer credentials (they were created during StealthMail deployment).
Click Login button.
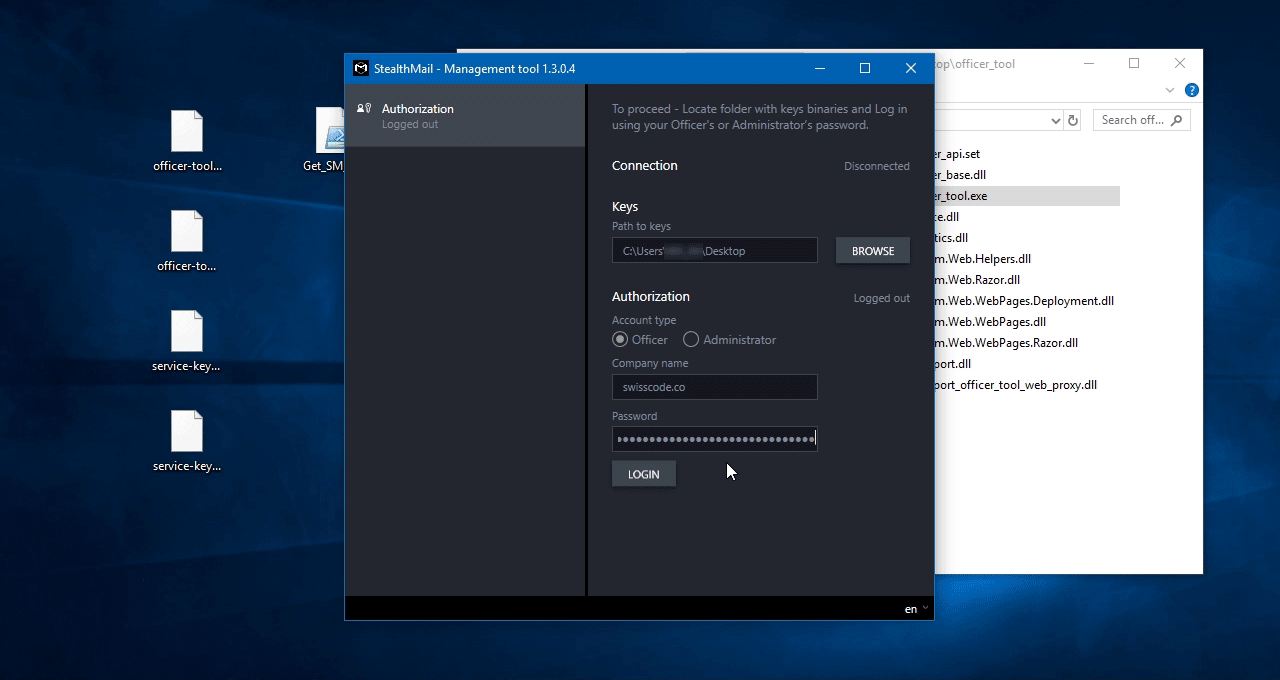
Congratulations! You have logged in to the StealthMail management tool.
To find more information about the tool’s capabilities, please refer to the user manual.