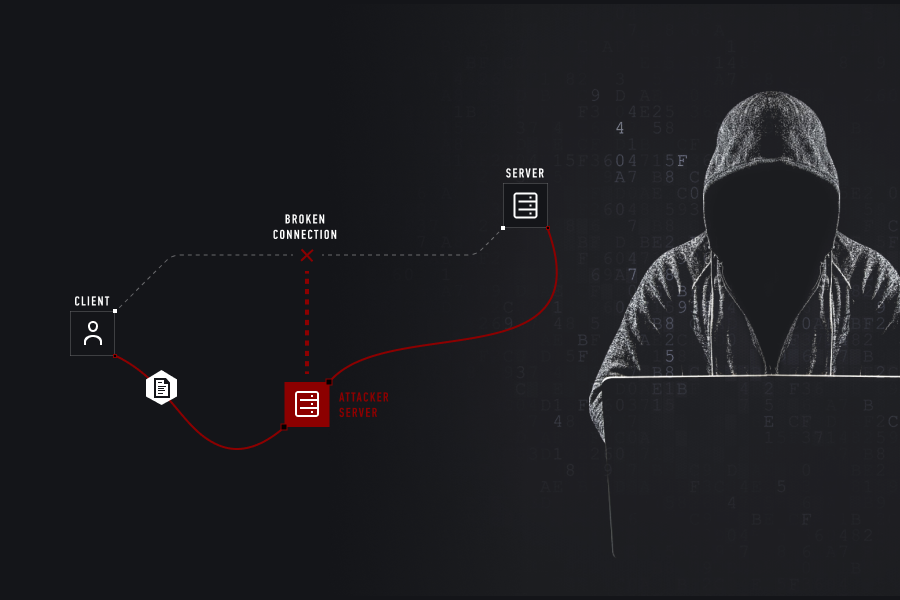
There are plenty of problems we face in our daily lives, but some of them are more obvious than others. One problem you might not even be aware of is your email – and the threat it poses to your organization’s cybersecurity. In particular, the threat of man-in-the-middle attacks.
That said, it’s important to first define the origin of a problem before you know how to deal with it.
So, let’s use the Five W’s principle and question our man-in-the-middle.
- Who is this man?
A cyber-criminal. - What is he after?
Your confidential data (email account credentials, credit card details, bank username and password, financial information, etc.) - Where is this middle located exactly?
Imagine, you are emailing your colleague. You are the only two parties (sender and recipient). No one must intervene in, overhear or even intercept your communication.
But our Man is a cyber-criminal. He has a mind of his own. He intercepts the contents of your message and uses the gathered information against you: he modifies it in whatever way he (or she) wants in order to extort more sensitive and valuable data from you (for example, to find out your bank credentials), and then sends an altered email to the recipient.
This leads you to think you are talking to your colleague, and your colleague to think he or she is talking to you. But in fact, all your communication is going through our Man. And that puts him in-between, or in the middle of your private conversation. Thus, you never know you are actually communicating to the cyber-pirate. - When does this attack take place?
Let’s say you received an email. It appeared to be from your bank. A bank officer is asking you to log in to your account to confirm your contact information. You click on a link in the message. The link directs you to the malicious bank’s website, where you log in and perform the requested task.
The man-in-the-middle is the one who pulls the strings.
In other words, cyber-pirates long and patiently prepare for these “events.” They use sophisticated strategies to steal confidential data, such as social engineering methods and phishing techniques. - Why does the man attack?
For the most reasons, your confidential data.
The more appropriate question is what will he do when he gets it? Well, the answer is terrifying: he will then try to hack your bank account and steal your money. Or demand a huge ransom for returning your data back unexposed. Or he might sell it to third parties. Or all of the above.
How Man-In-The-Middle Does It: Types of the Attack
Email Credentials Hijacking
Applications use a password-login pair mechanism that generates a temporary session token. An attacker listens to sensitive traffic to identify the session token and intercepts it.
This type of attack can happen on both an individual and organizational level. When an attacker breaches an email account, he then monitors communication between the two parties, trying to get information sent to their accounts and steal data from users related to the breached account.
Packet Sniffing
Using radio devices, a cybercriminal can monitor and obtain a significant amount of information about users, their transactions, and their accounts.
If the account’s textual information is unencrypted, such as logins and password, it can be read or possibly used for blackmailing the communicating parties.
Cyber Infections
Cyber Infections are a type of MITM attack in which malicious software is installed into devices to gather information, redirect traffic, or shut down systems. Cyber infections can occur through emails, system extensions, or networks.
Packet Injection
An attacker monitors a user’s device to inject malicious packets into data communication channels. The packets could mix up with valid data, appearing to be a part of the communication. Usually, packet injection involves packet sniffing to determine how and when to send packets.
How Outlook’s Protection Does It: Digital Signatures You Probably Haven’t Heard About
A digital signature identifies you as the message signer and allows the recipient to verify that contents have not been altered from the moment you signed it.
To send and view encrypted email messages, you and the recipient need to share with each other your public key certificates. To enable the encryption of email messages, you need to send a digitally signed document.
Email encryption in Outlook is S/MIME. S/MIME stands for the Secure/Multipurpose Internet Mail Extensions (a standard for public key encryption).
In S/MIME, email messages can be signed or/and encrypted. Messages are encrypted with the public key of the recipient of the message. That ensures that decryption of the message is done only with the recipient’s private key.
Digital signing of the email is also done with the sender’s private key. That ensures the sender’s identification. When the recipient opens the email, the sender’s public key is used to verify the signature. This way, the recipient can be sure the emails really came from this sender.
In order to use S/MIME encryption, one must obtain a certificate from the trust center, also known as certificate authority (CA).
But consider some nuances when using S/MIME encryption:
- S/MIME uses end-to-end security, which means that it is not possible to determine whether the content in the message holds the malware or not. However, if an email is not inspected for malware at a company’s gateways, encryption will successfully bypass the detection and deliver the malware.
- Encryption may be performed with a public/private key pair only, without need in using certificate implementation.
How to Protect Emails from MITM Attacks: StealthMail Gives an Answer
The fundamental principle of communication is the secrecy of correspondence. It guarantees that the content of sealed letters is never to be revealed. Whether letters are in transit or at rest, they are not supposed to be opened by third parties.
StealthMail delivered a solution that is designed to protect the key principle. It is called the StealthMail Add-In.
The StealthMail email security solution:
- Is based on the identification of both parties: the sender and recipient.
- Provides Email Certification and Digital Signatures operations.
- Uses asynchronous key generation algorithms (ECC, RSA), encryption, stream ciphers, advanced data encryption algorithms (AES, Twofish).
- Utilizes self-developed and patented data transfer protocol (Secure Dynamic Network and Protocol).
- Excludes the actual transferring of the content and its attachments. Instead of sending data directly, the solution sends a link only, which refers to it. By its design, a link is useless and does not comprise any payload.
- Is not influenced by the attack by any means (if you are a StealthMail’s user, to commit an attack is simply impossible).
To allow communication between two parties with StealthMail, the sender and receiver must have their “passport.”
In the StealthMail Add-In the “passport data” is a multi-stage identification process of each participant. Only when both sides have confirmed their ID’s and, thus, were recognized by the service, they will be able to continue communication.
To read a message, the application installed on the recipient side performs the same operations as when a letter is sent. It is fair to say that to read a message, the application checks the “passport data.” After confirmation of the identities has been completed, the service decrypts the message.
In other words, with the StealthMail email security solution installed on your device, the chance to execute a phishing attack equals zero, i.e. impossible, because you know for sure that the one who writes you is the real sender.
To get more broader technical insights of StealthMail and how the solution can help protect your business email-correspondence, please download datasheet at https://StealthMail.com/en/info.
Link copied to clipboard!