There are a lot of email security services on the market, and most of them deserve some spotlight.
Nobody would get in trouble for finding out more information about information security, but today people just don’t know where to start.
When we are stepping into the sea of new information, it makes sense to enter the unknown environment slowly, methodically. Email security, in particular, is not easy for the public to get into, or simply “get” at all.
Why do we need it? Let’s markdown why exactly email security matters.
“Nobody Will Ever Try To Hack Me, I’m No Big Fish!”
That’s a very popular objection.
Everyone thinks they’re safe for one simple reason – “they have nothing to hide”, or there’s too much fish in the sea for anyone to even notice them.
True, to some extent, but you might want to know that cybercriminals don’t look out for you in particular when hunting for credit card information, protected health information, or addresses you’ve contacted.
Mass phishing attacks or credential stuffing techniques are not targeted attacks, but they give malicious actors a lot of personal data to work with. Those are two of the fastest and easiest ways to compromise your email account, and it comes downs to quantity, not quality.
It’s also important to note that there’s too much noise, data breaches, privacy concerns happening in 2019. People have become desensitized to the point they understand the threats, but still ignore the looming danger.
We hear stories about big corporations getting intruded by hackers every week; it’s hardly a surprise now. Media hunting for big headlines can make us believe that only big corporations are being subjected to cyberattacks, but that’s simply not true.
Email Security Concerns Companies Of All Sizes
According to the Verizon 2019 Data Breach Investigations Report, 43% of cyber-attacks target small businesses.
Reason is fairly simple – lesser companies don’t have enough budget and resources to fight back or even cover up properly. Security and data protection take a backseat in the wild ride of small and medium businesses.
Let’s take Otto Pizza’s case – this pizza company was an easy victim for targeted attacks, and while it didn’t have the financial status of companies like Domino’s or Papa John’s, it still had a lot of confidential info at its disposal. A successful takeover of their email system resulted in 900+ credit and debit card numbers leaked. The stolen information was sold on, and the fraud wasn’t reported for many months, which is a regular practice in such occurrences.
There’s not enough knowledge about these problems, not enough action taken to investigate cyberattacks that have already happened, no strive to stop being the “lowest hanging fruit”.
The damages companies can experience in case of similar attacks are not always compatible with a normal working process.
What Could We Do To Reinforce Email Security?
You can’t figure out everything with only one technical solution.
The most important requirement for effective email protection is undoubtedly user education, awareness, and willingness to disclose errors or identify suspicious activity from end-users. That’s a basis you can’t build anything without, it’s fundamental.
And even then, the foundation is not everything either, you need walls, roof, locks on the doors. Email is the door into any company in the world.
It is an Internet-facing area that is in constant human use, it falls into a category of boundary traversing systems that are critical. If you don’t have the tools or capability to monitor or restrict data – you’re at significant risk.
For effective email security, you need encryption software, email security gateway, data loss prevention system, spam filters, antiviruses too. Some companies even acquire TLSI to monitor the data at all times.
Email security services need to address a real threat and be user-friendly, as no matter how technologically sound they can be, if people won’t use them – there would be no sense in owning them.
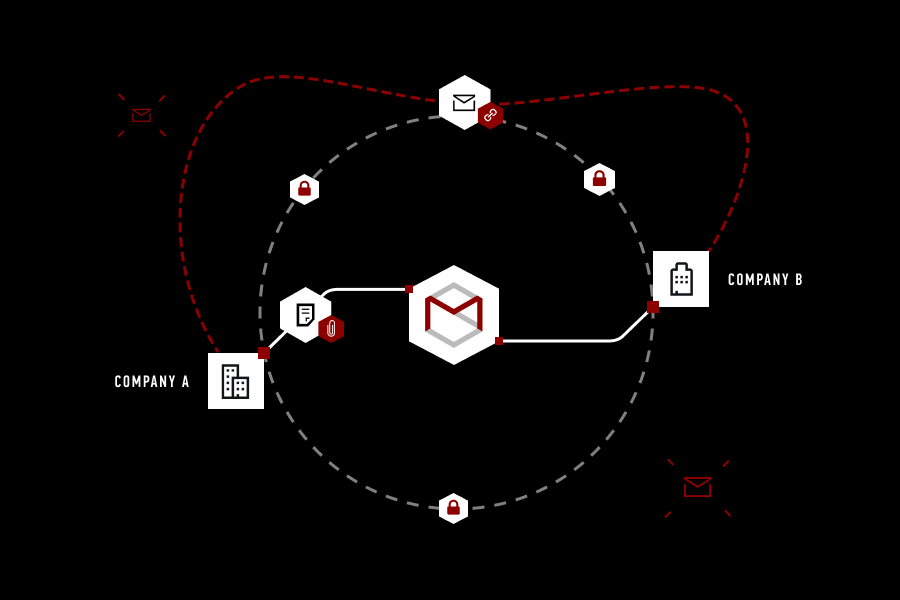
We kept that in mind when designing an email security service StealthMail.
The Goal Of StealthMail’s Email Security Solution
When we mentioned email security criteria every company should address, we mentioned encryption first.
Email encryption is practiced to ensure that your confidential data and sensitive files are protected from outsiders. The encryption procedure from the past required a lot of time and effort from users, but now those days are long gone.
Today we have an abundance of products talking all about end-to-end encryption that seemingly provides us with a guest-free line of communication.
Unfortunately, it’s not always the case, as encryption keys that enable secure communications are not under the control of users. StealthMail fixes this email security issue, giving companies full control over their encryption keys and encryption processes.
StealthMail gives you more than just a secure channel for data transferring, it ciphers your content inside of the said channel, and keeps it inside your own company.
While StealthMail takes up a fairly innovative approach to data protection, it’s integration only takes a couple of hours and still leaves you with a familiar Microsoft Outlook interface.
For more information about this email security service and its primary features, please download datasheet at https://StealthMail.com/en/info today.
Link copied to clipboard!