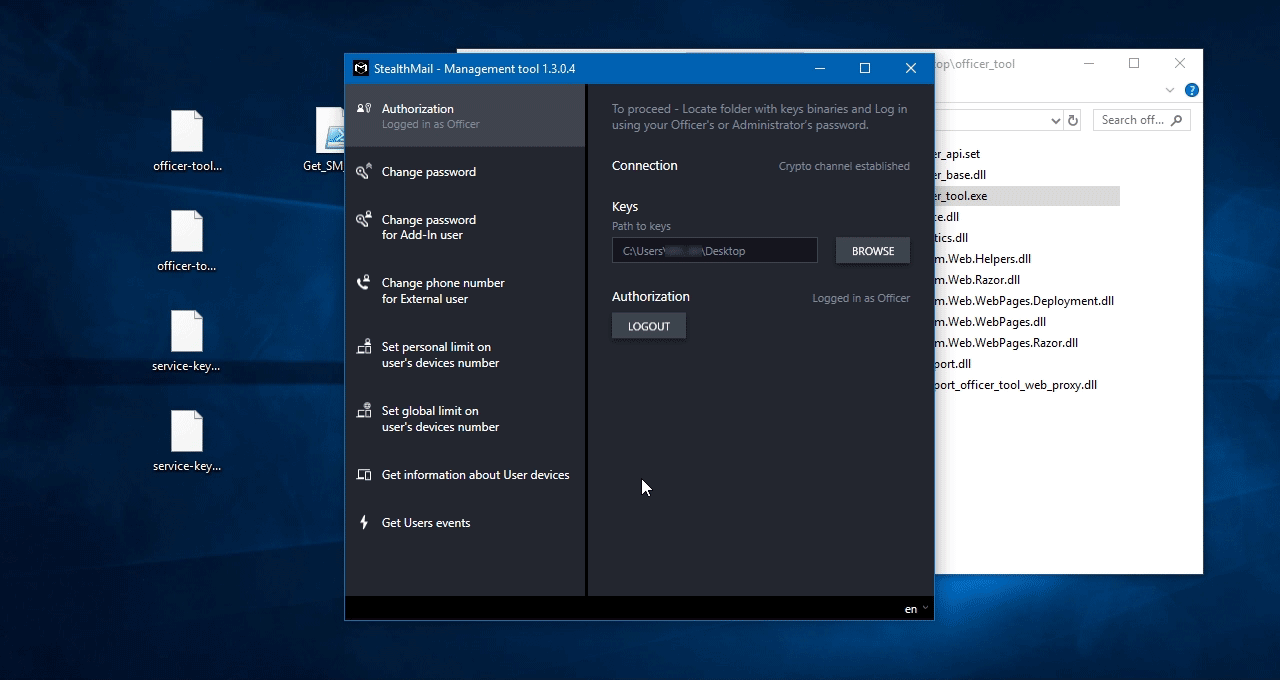
Officer tool
StealthMail Officer Tool - это приложение, позволяющее управлять пользователями StealthMail: изменять пароли пользователей, указывать номера телефонов для внешних пользователей, устанавливать лимиты на устройствах пользователей и просматривать пользовательские события.
Чтобы администраторы и офицеры службы безопасности Вашей компании могли его использовать, сначала необходимо экспортировать секретные ключи. Они будут использоваться администраторами и офицерами службы безопасности для входа в систему. Наряду с ключами доступа будут экспортированы и служебные ключи. Эти ключи используются для дополнительной защиты хранилища зашифрованных данных пользователей и компании.
Внимание: Сохраняйте ключи в защищенном хранилище. Если что-то случится с хранилищем Azure, Вы сможете перезагрузить их из резервной копии.
Получение прав на экспорт ключей
На портале Azure перейдите в группу ресурсов, которую Вы создали во время установки StealthMail.
Нажмите Resource groups в списке, затем в появившемся фрейме нажмите на группу ресурсов StealthMail.
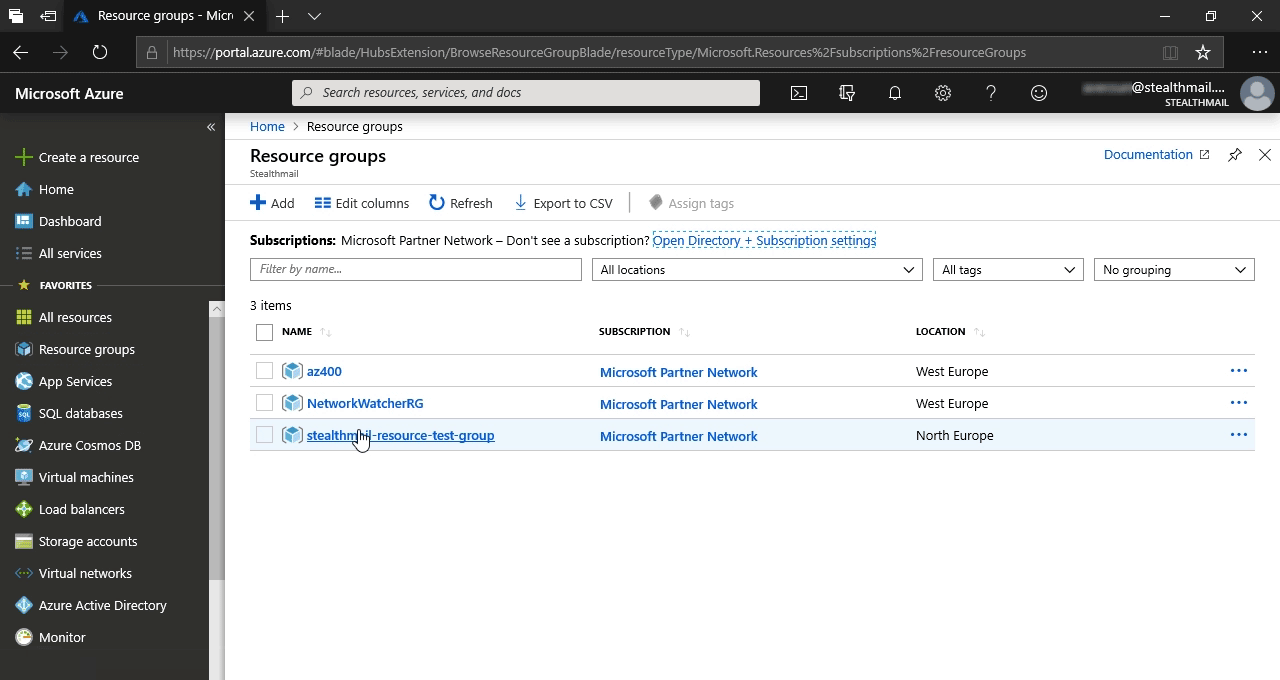
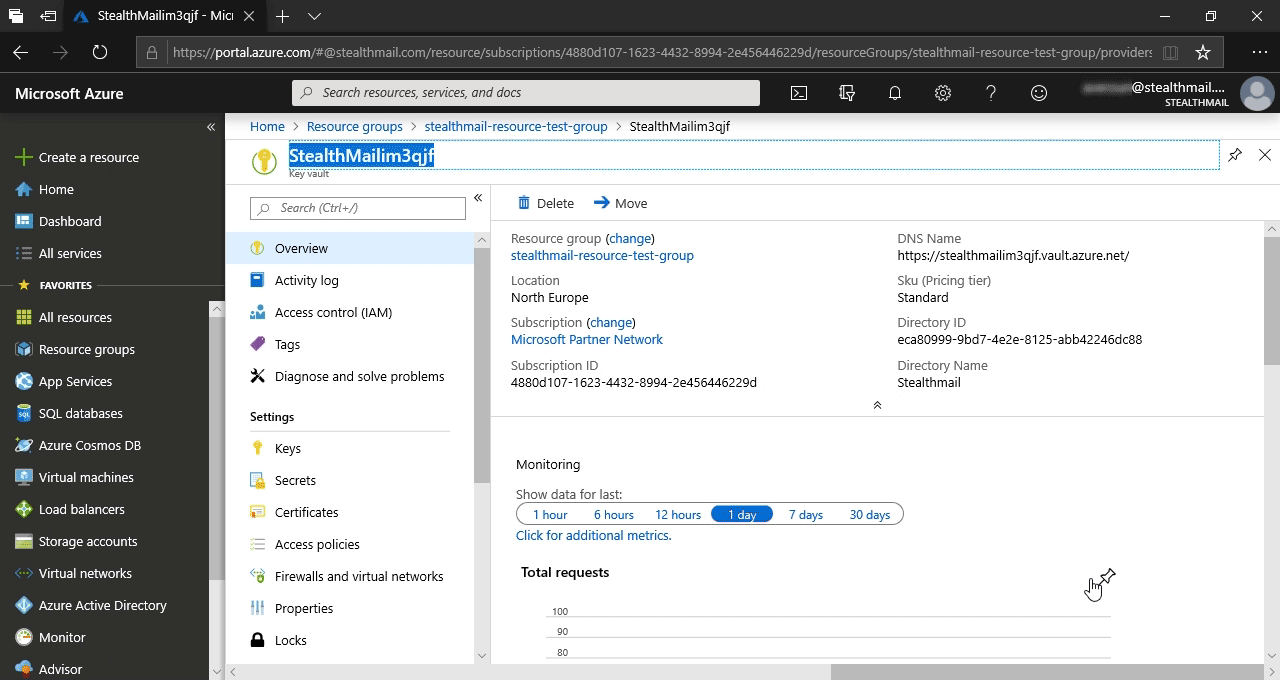
Прокрутите список вниз до пункта Key vault StealthMail#######, где # - случайный символ или цифра.
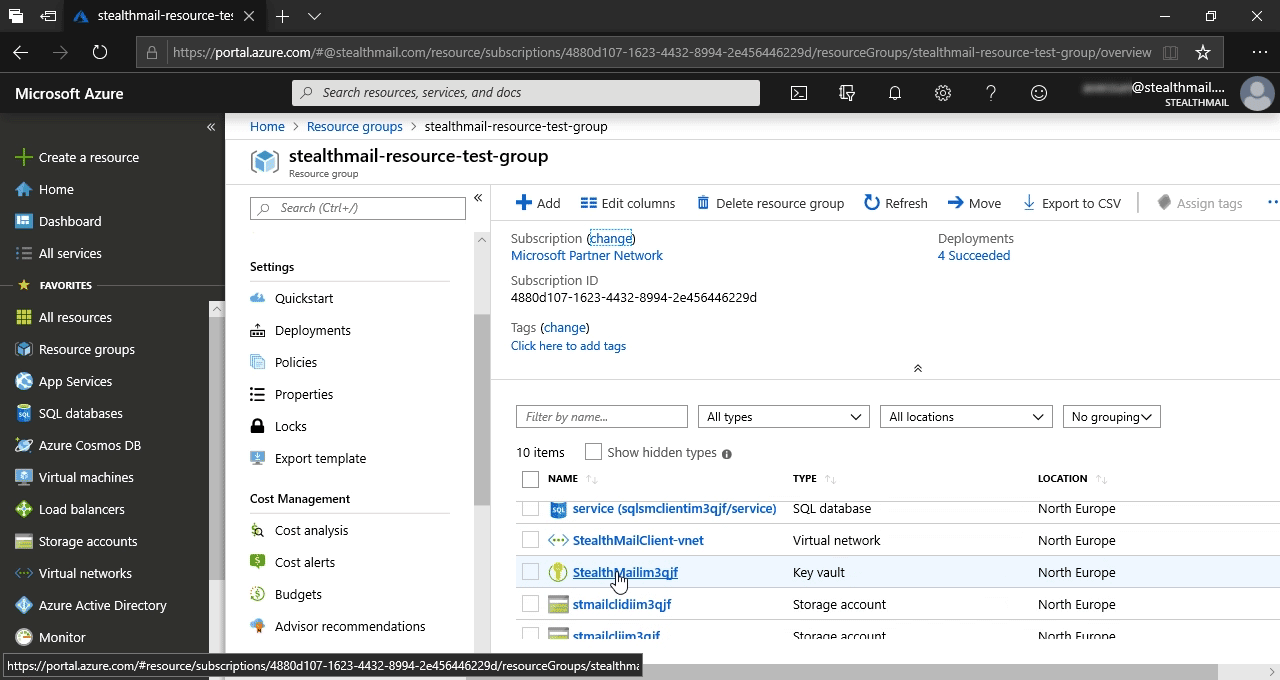
В списке найдите и нажмите на Access policies.
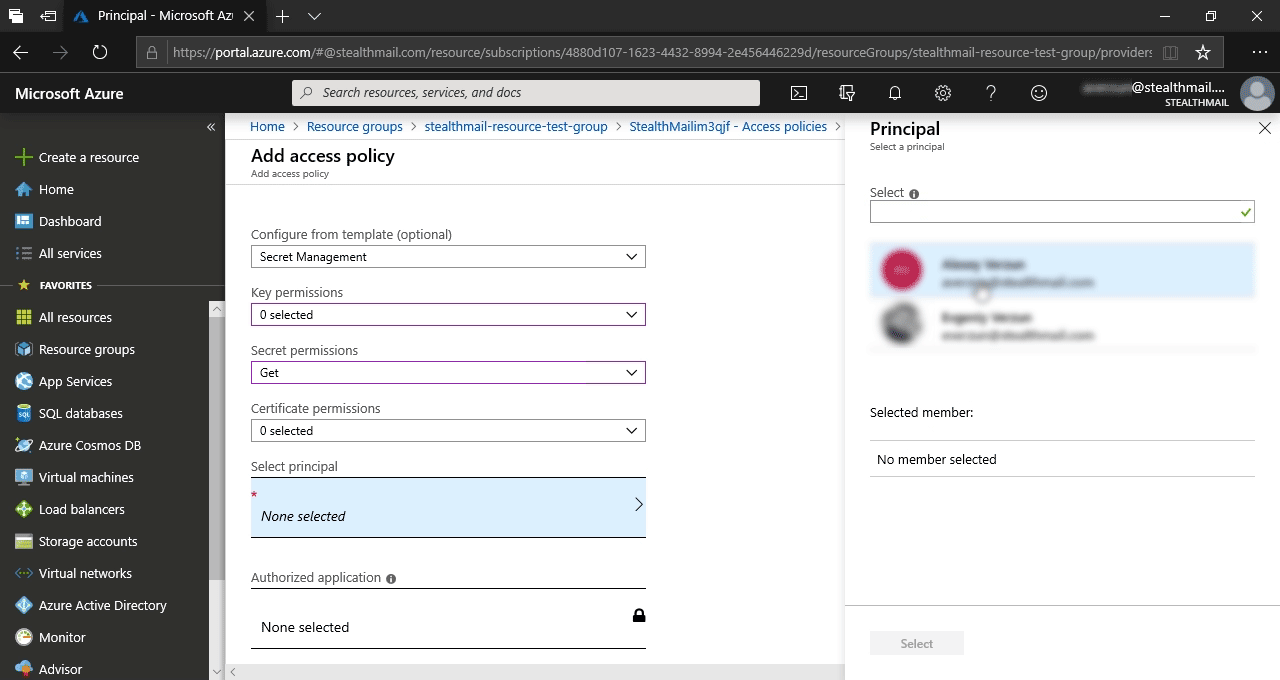
Затем в появившемся фрейме нажмите на + Add Access Policy.
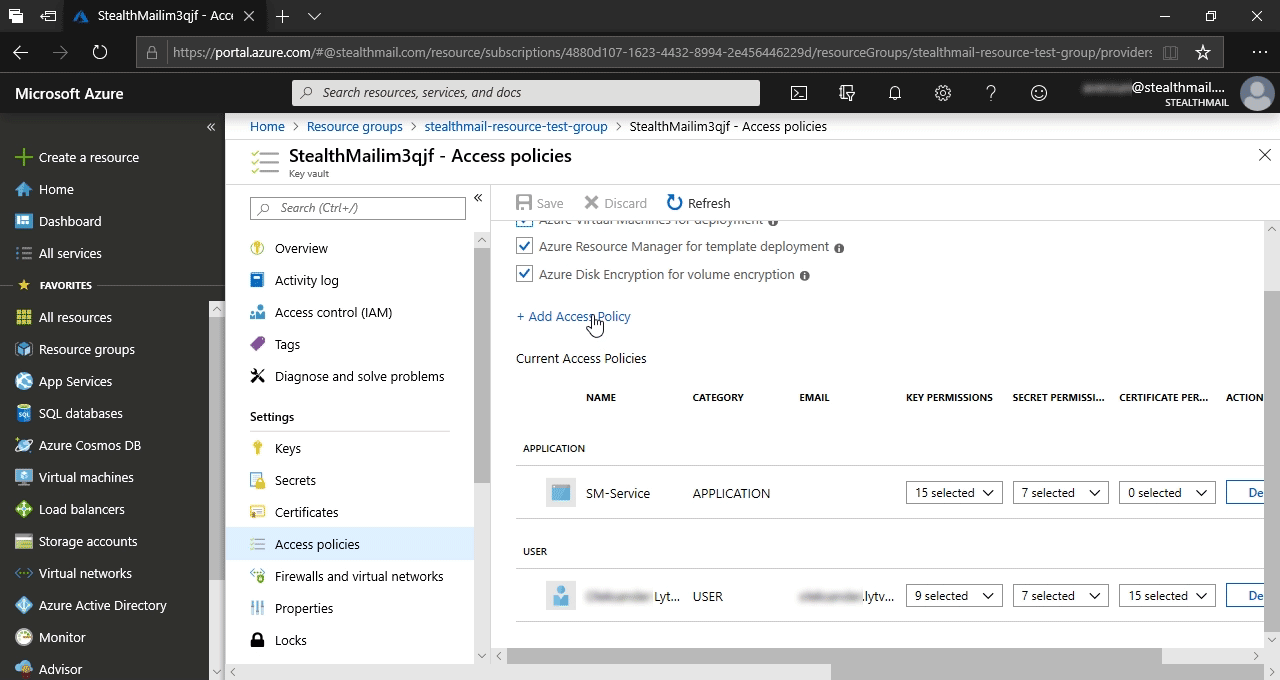
В открывшейся фрейме заполните форму следующим образом:
- В поле Configure from template - выберите Secret Management;
- В поле Secret permission - выберите Get;
- Нажмите кнопку Select principal и в правом фрейме выберите учетную запись пользователя, которая будет использоваться для экспорта секретных ключей, затем нажмите кнопку Select.
- Остальная поля оставьте со значениями по умолчанию.
- В самом низу основной формы нажмите кнопку Add.
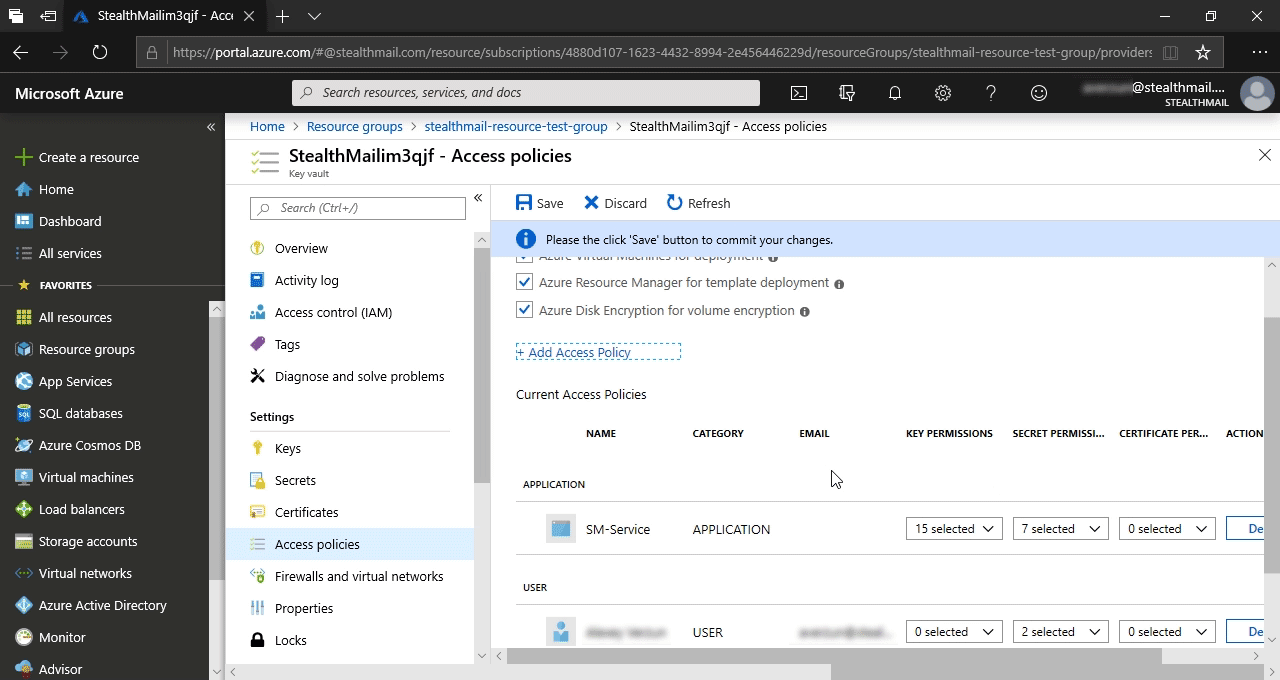
Вы будете переадресованы назад в Access Policies.
Нажмите кнопку Save.
Теперь Вы готовы к извлечению секретных ключей.
Извлечение ключей
Получите скрипт PowerShell для извлечения ключей, используя одну из ссылок:
Get_SM_Keys_From_KeyVault.ps1- для последних версий Windows 10, Windows Server 2016/2019.
Get_SM_Keys_From_KeyVault_AzureRMbased.ps1- для ранних версий Windows.
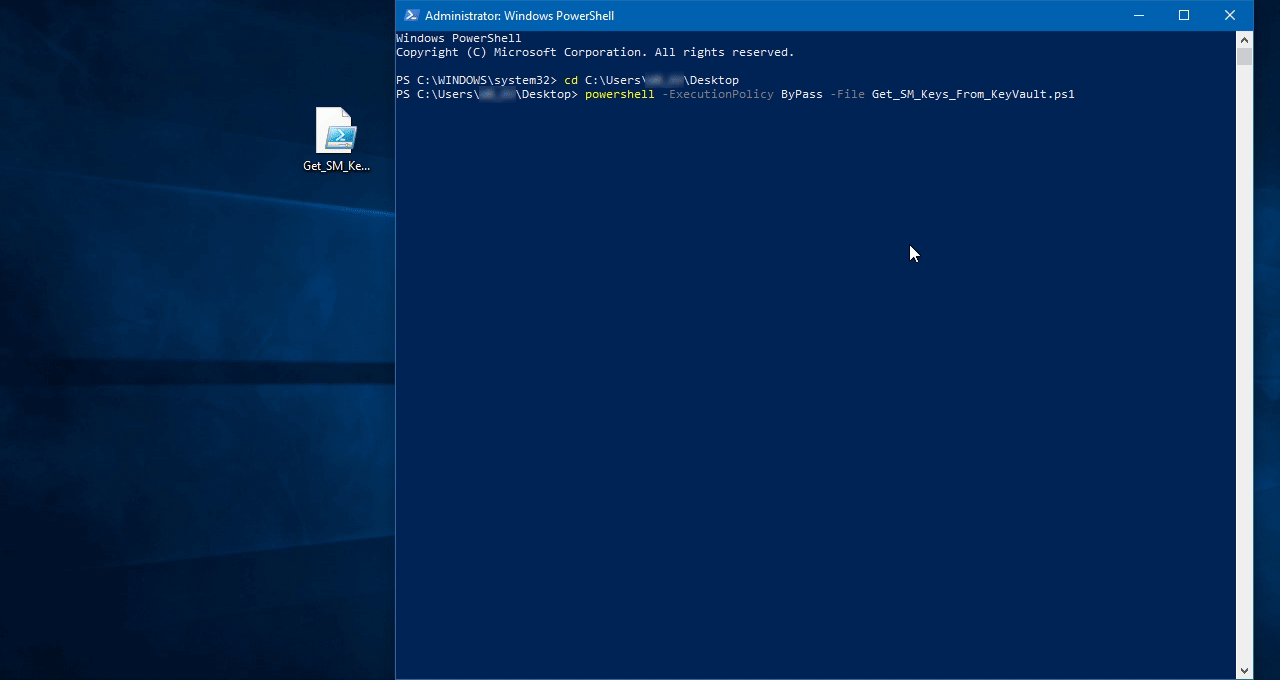
Запустите PowerShell с правами администратора.
Затем запустите скрипт следующей командой:
powershell -ExecutionPolicy ByPass -File Get_SM_Keys_From_KeyVault.ps1, где параметр -File должен содержать путь к powershell.
Введите путь назначения и имя KeyVault StealthMail####### из группы ресурсов StealthMail.
Возможно, что в Вашей системе не окажется необходимых модулей и Вам будет предложено разрешить их загрузку из репозиториев Microsoft.
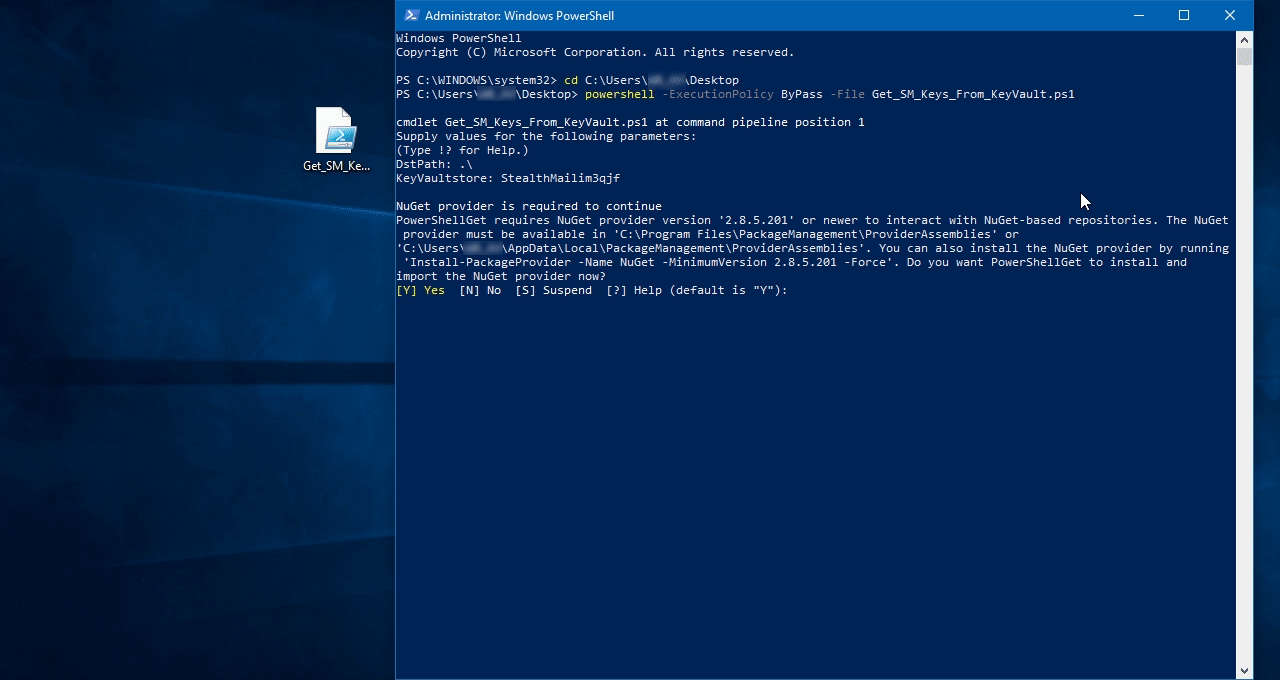
Используйте Ваши учетные данные, которые Вы предоставили в качестве основных во время предоставления прав доступа на предыдущем шаге. Это необходимо для доступа к StealthMail KeyVault и извлечения секретных ключей.
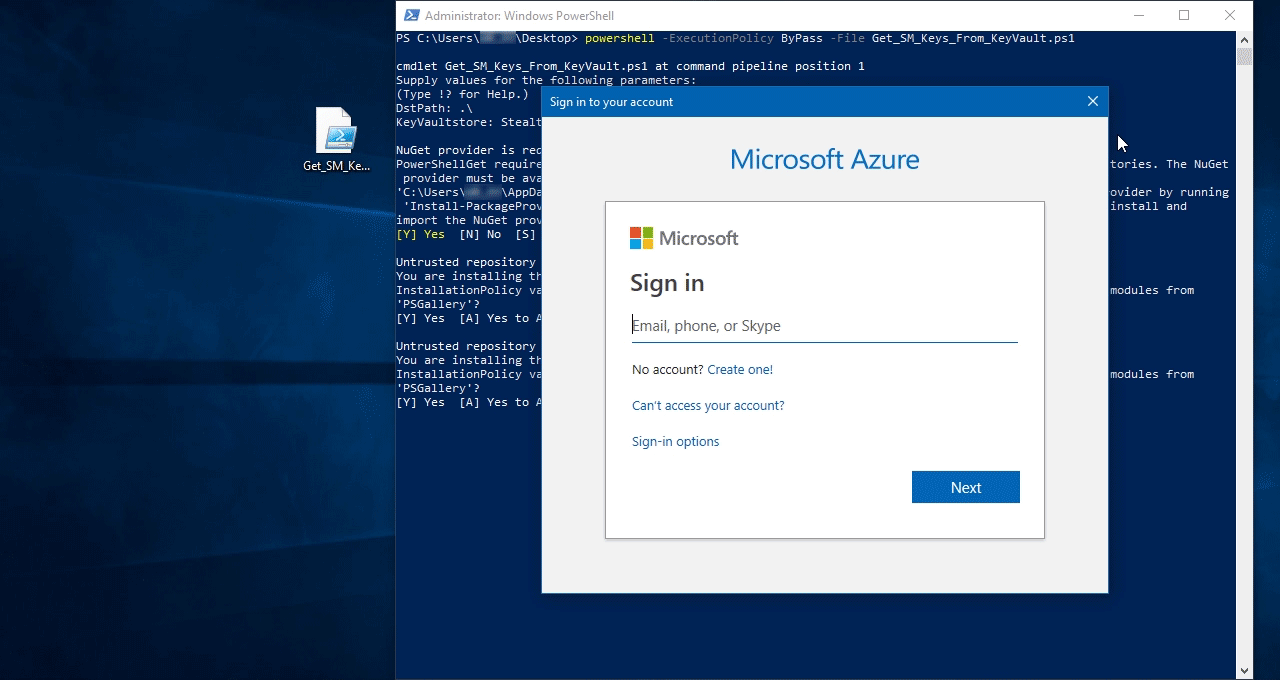
В результате Вы получаете секретные ключи доступа администратора и офицера безопасности:
- officer-tool-officer.bin
- officer-tool-admin.bin
Эти ключи будут использоваться в инструменте Office Tool для входа в систему и управления пользователями StealthMail.
И пара сервисных ключей:
- service-keys-manager-officer.bin
- service-keys-manager-admin.bin
Эти ключи используются для дополнительной защиты хранилища зашифрованных данных пользователей и компании.
Внимание: Сохраняйте ключи в защищенном хранилище. Если что-то случится с хранилищем Azure, Вы сможете перезагрузить их из резервной копии.
Следующий шаг: загрузка и настройка Officer Tool для первого запуска.
Запуск Officer Tool
Скачать приложение Officer Tool.
Откройте officer_api.set с помощью любого текстового редактора.
Для officer_api_webProxyIp необходимо задать IP-адрес ВМ, на которой установлена StealthMail.
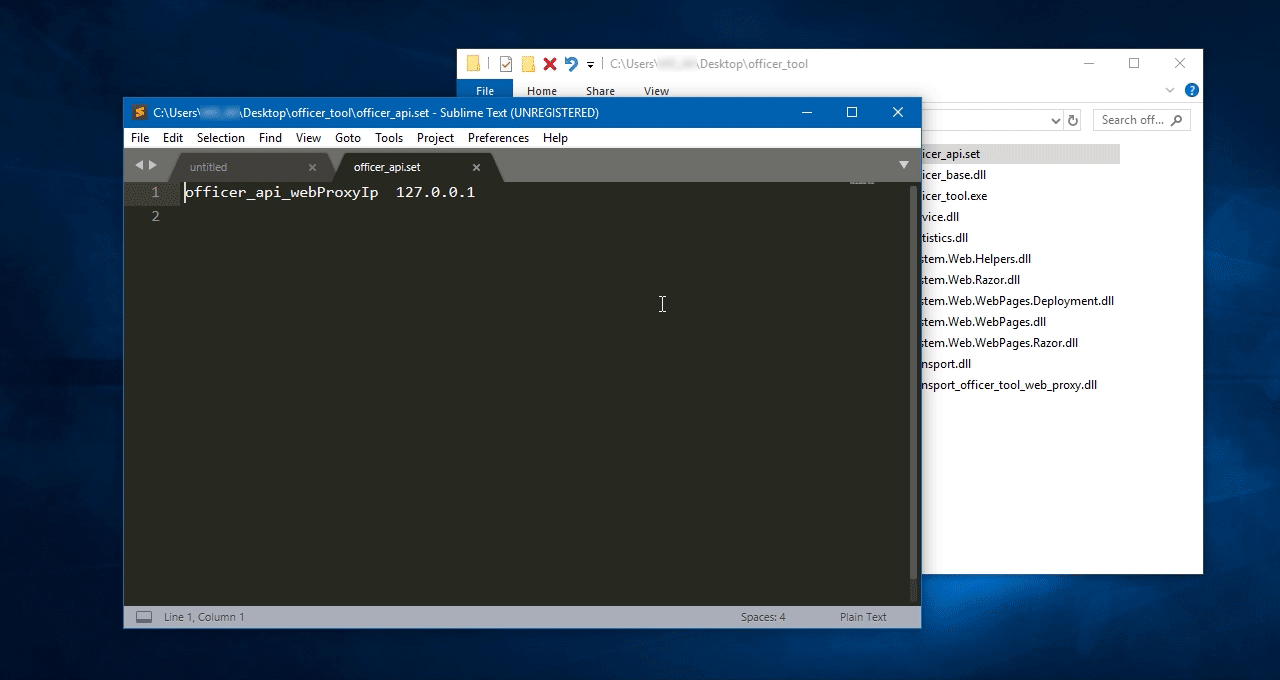
Чтобы получить IP адрес ВМ, вернитесь в группу ресурсов StealthMail и пролистайте список до пункта списка ВМ SM-Service VM и нажмите на него.
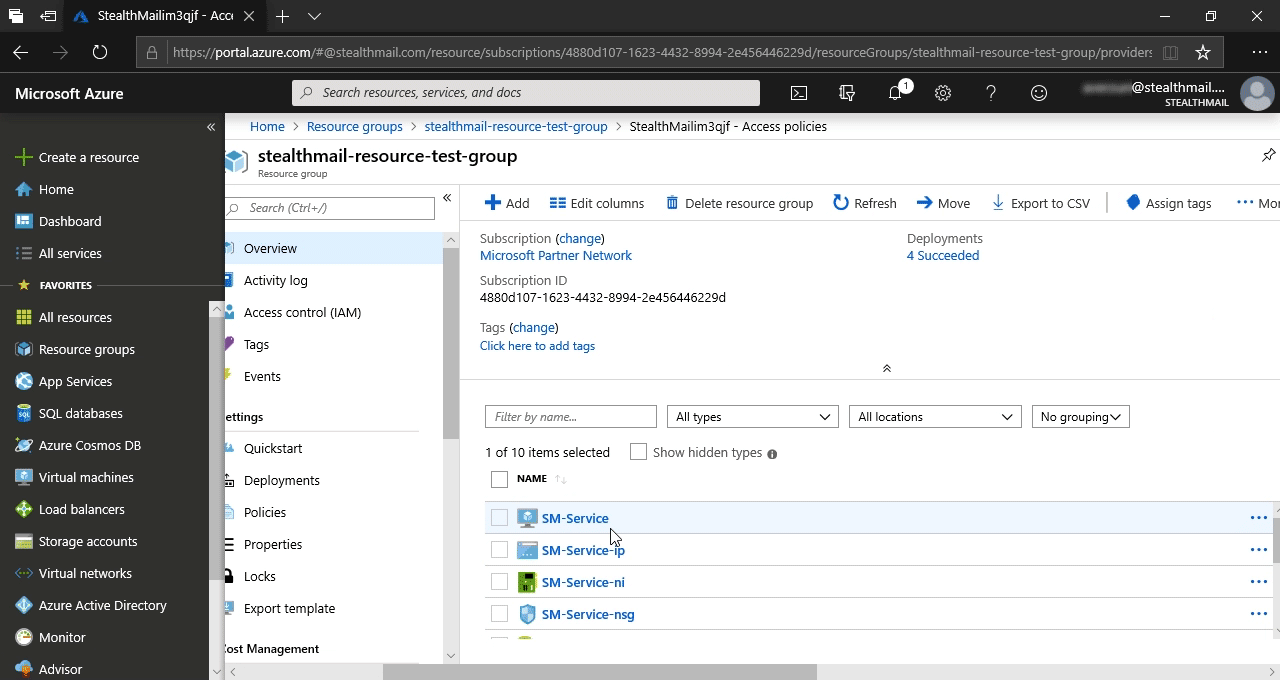
Скопируйте Public IP address и вставьте его в открытый officer_api.set.
Сохраните изменения и закройте файл.
Запустите officer_tool.exe
Для входа в систему выберите папку, в которой сохранены извлеченные ключи доступа.
Введите учетные данные администратора или офицера службы безопасности, созданные во время установки StealthMail.
Нажмите кнопку Login
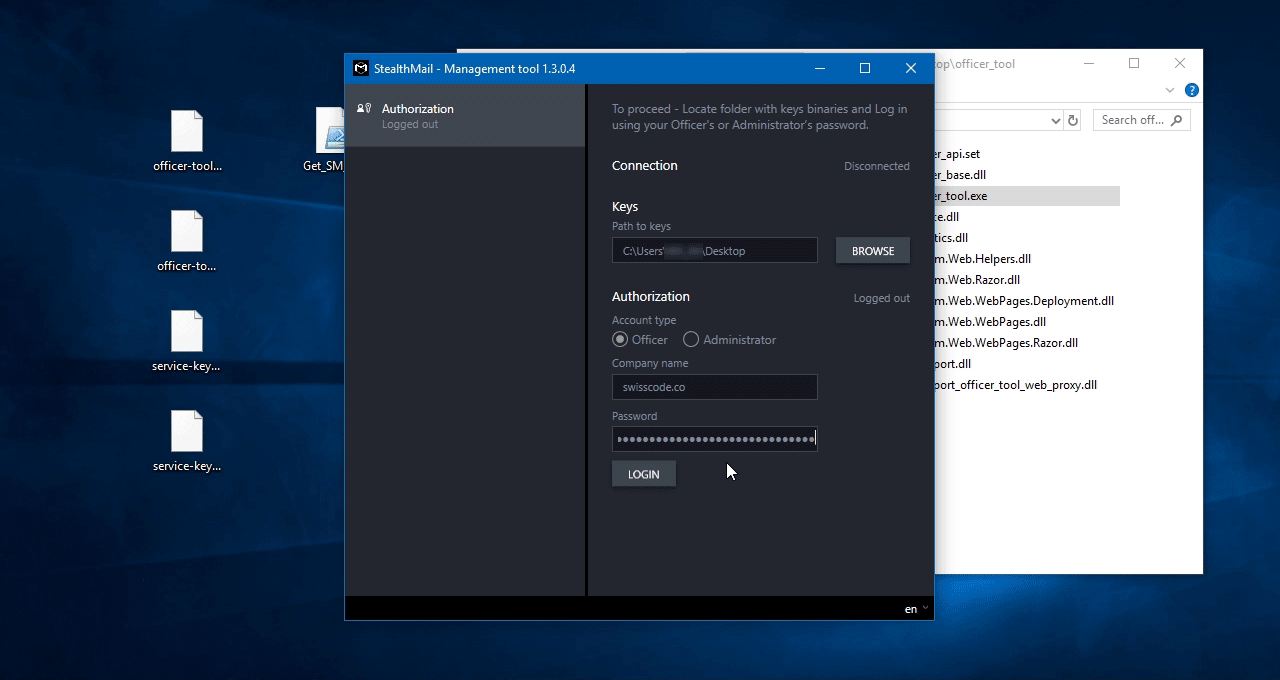
Поздравляем! Вы успешно запустили Officer Tool.
Чтобы узнать больше о возможностях инструмента, обратитесь к руководству пользователя.